- Print
- DarkLight
- PDF
Analytics - Requests
- Print
- DarkLight
- PDF
In this article, we’re talking about a key monitoring feature in your Azure API Management, Analytics feature, with a deep dive on the Requests section. Looking at this diagram, you can get plenty of information about different request being sent to your API Management.
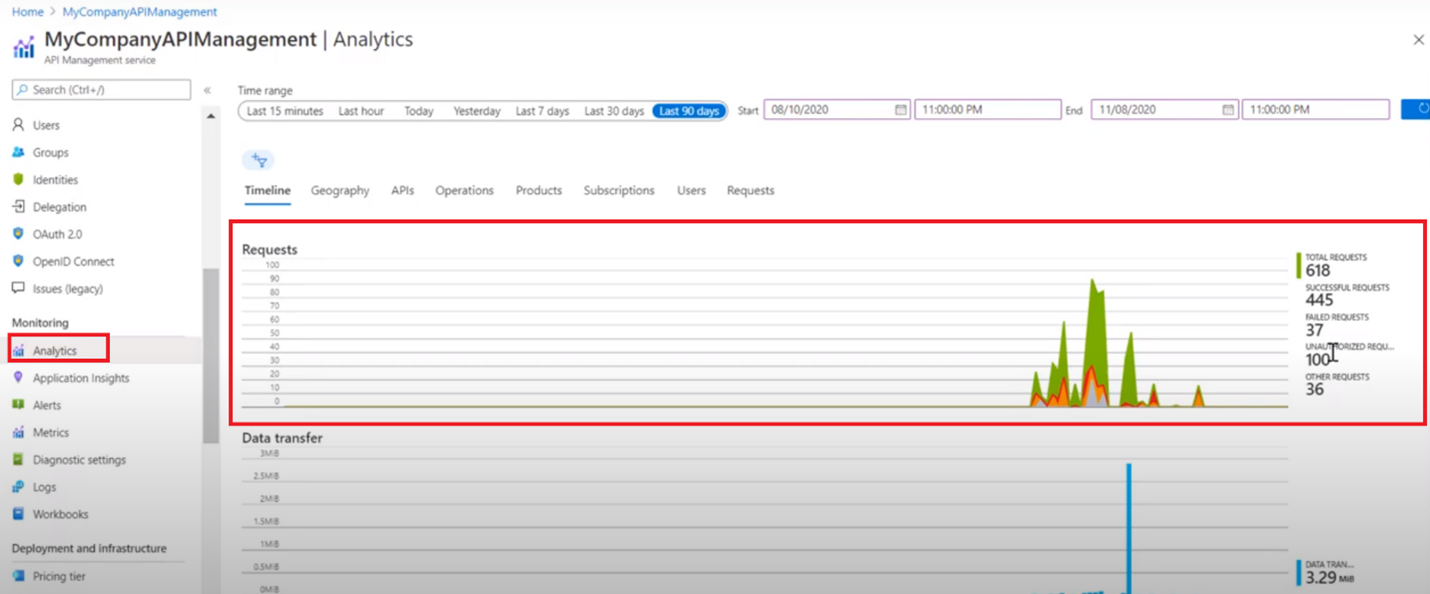
- Total Requests: the total number of requests that’s been sent to your API Management.
- Success Requests: the number of successful requests that’s been sent to your API Management.
- Failed Requests: the number of failed requests that’s been sent to your API Management.
- Unauthorized Requests: the number of unauthorized requests that’s been sent to your API Management.
You need to pay attention to the difference between Failed Requests & Unauthorized Requests.
Failed Requests: are genuine requests being sent to your APIM, and for some reason, your APIM instance had failed to fulfil these requests, it may be because of timeout, backend service unavailability... You need to keep an eye on the number of failed requests and always reduce the failed requests number that your APIM is getting.
While Unauthorized Requests are requests that are not authorized, it could be one of two cases:
- Either it’s a genuine request from a trusted system. Still, this trusted system uses a wrong subscription key, and you can fix this quickly by confirming that the trusted system is using a valid subscription key to call your APIM instance.
- Or someone is trying to hack your APIM instance, by trying different subscription keys and hoping that one of these subscription keys might get them to use your APIM instance. To mitigate this attack, you could set up an Alarm that watches for “number of unauthorized requests” metric. So, when the number of unauthorized requests exceeds a certain limit, your Alert would notify you about this unusual increase of unauthorized requests. Then, we could take it to the next step, and involve your network engineers, and security team to see who’s trying to break into your APIM instance, and how you could block them.

