- Print
- DarkLight
- PDF
App Proxy for Cloud identity and access management
- Print
- DarkLight
- PDF
Providing a seamless user experience while still securing identity is a delicate balance. Users want a single sign-on experience for their access to resources, both on-premises and the cloud. This article goes through the process of configuring Azure AD application proxy to migrate on-premises applications to Azure AD for authentication and SSO.
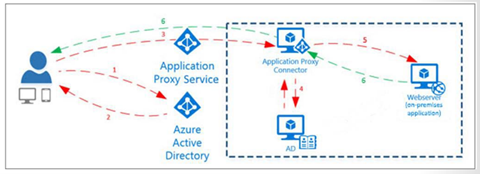
Azure AD application proxy provides integration between Azure AD, the on-premises application and the authentication settings in Windows Active Directory. Figure 1 is a diagram that shows how Azure AD App proxy works. The difference between Azure AD app proxy and hybrid identity architecture through Azure AD Connect is a single registration for a single on-premises application. Rather than having a synchronization between Windows AD and Azure AD for authentication and authorization, the Azure AD application proxy service is used to pass the credentials to Azure AD for the user to authenticate. The application proxy service makes the on-premises application emulate a cloud application in Azure AD. This provides the SSO authentication through Azure AD along with Microsoft 365 and other registered cloud applications as the single identity provider.
The role required to perform this configuration is an Application Administrator or Global Administrator. Adhering to the principle of least privilege, you should assign users that need to perform this configuration with the Application Administrator role. Once you have that role activated, you can begin the configuration as shown in the steps provided within this tutorial on Microsoft Docs: https://docs.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-add-on-premises-application.
Going through the steps of this tutorial will help in adding the application to Azure AD and can be for SSO. It is important to note that the application proxy connector should be installed on more than one device in your on-premises network for additional resiliency in case of a device failure. The application can now be used with Azure AD credentials for user access, similar to other cloud applications like Microsoft 365.

