- Print
- DarkLight
- PDF
Blocking Inbound IP addresses in Azure Logic Apps (Standard) using Access Restrictions
- Print
- DarkLight
- PDF
In a previous Serverless Notes post, I discussed how you can restrict access, via IP Address, to your Azure Logic Apps (Consumption) instances. In this post, we are going to discuss how we can achieve something similar, but in Azure Logic Apps (Standard).
Why do I want to restrict access to my logic app triggers?
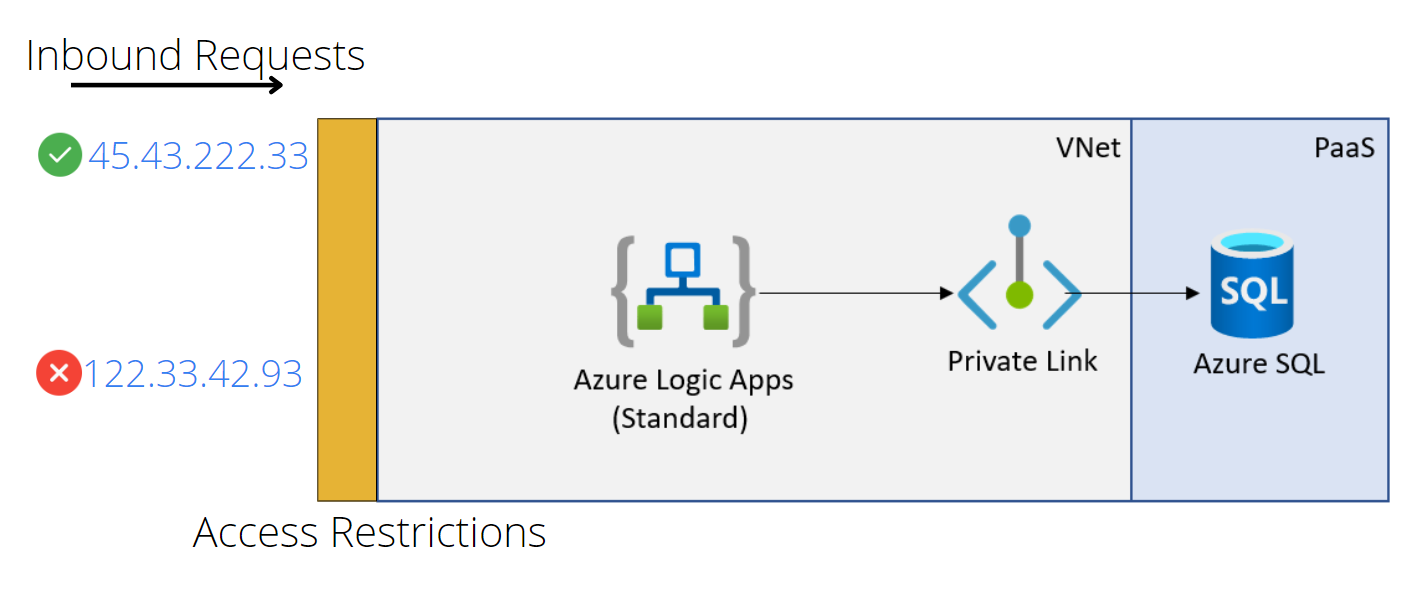
By default, when you expose a logic app HTTP Trigger, it is available over the public internet and contains a SAS token as part of the URL. This makes it very convenient to share with someone who needs to call your logic app. For some organizations, this creates a concern as it means that your logic app can be called from other public networks.
By using Access Restrictions feature, you can restrict where people are making requests from. This could be from your local corporate network or from a trading partner’s network. This greatly reduces the surface area and reduces the risk of unauthorized people calling your endpoint.
Using this feature, we can create a list of rules that allow certain IP address ranges to contact our service. Otherwise, we can also explicitly create block lists as well if we have known bad actors that we want to prevent communication with.
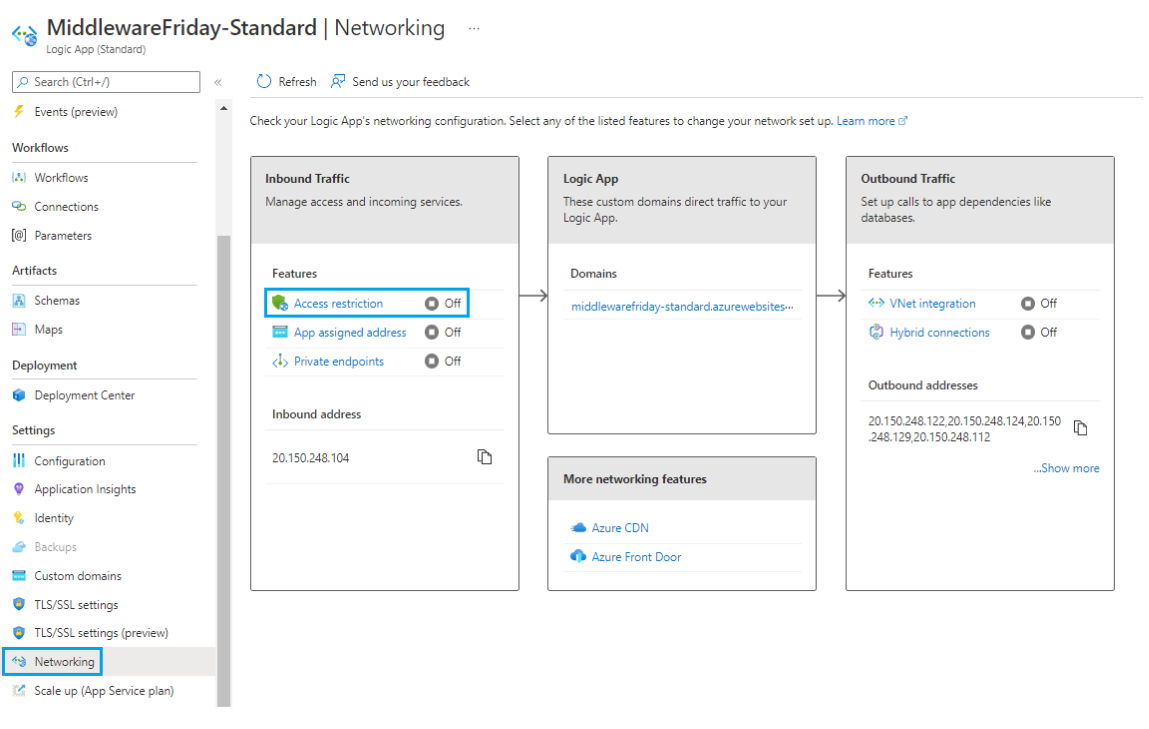
To enable this feature, access the Networking link from your Azure Logic Apps (Standard) instance and then click Access Restriction.
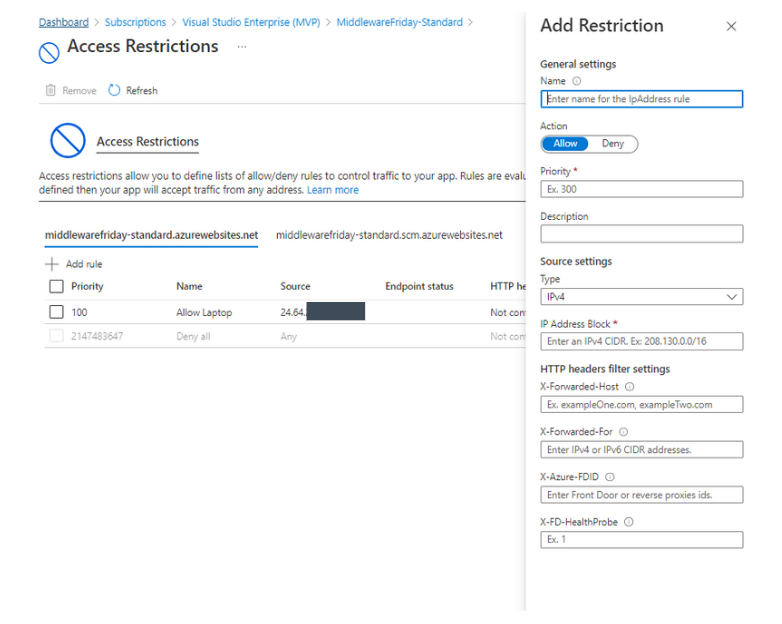
At this point we can now create one or more rules that allow us to either Allow or Deny requests from specific IP ranges. In addition, we also have additional filter settings for HTTP headers and forwarding settings.
To see a demo of this feature, please check out the following YouTube video: Blocking Inbound IP addresses in Azure Logic Apps (Standard) using Access Restrictions.