- Print
- DarkLight
- PDF
Managing Connectors using Directional DLP
- Print
- DarkLight
- PDF
I recently ran into a situation where a customer wanted to use the Azure AD connector, but they wanted to ensure that only read operations could be utilized. When it comes to connectors, it is important to understand that the connector will not elevate anyone’s access. So if a user only has read access to the data source, the connector will not give them additional privileges when their credentials are used to create a connection. However, this wasn’t the ideal solution for them.
While applying the appropriate permissions (least required privileges) is a good practice, administrators can also use Data Loss Prevention policies from the Power Platform Admin Center to govern connector access. Historically, DLP policies were managed at the connector level and not the individual operation level. But, this is no longer the case and the Power Platform now provides more granular control. This allows an admin to restrict specific operations including ones that provide read vs write access.
Solution
If we want to govern the Azure AD connector, for example, we can access the Power Platform Admin Center as an administrator (Environment, Power Platform or Tenant). From there we can select Data policies, our DLP policy and then choose to edit this policy. Next, we can click on Prebuilt connectors and then look for our specific connector. In this case, Azure AD. From there, we can click on the ellipses … and then select Connector actions.
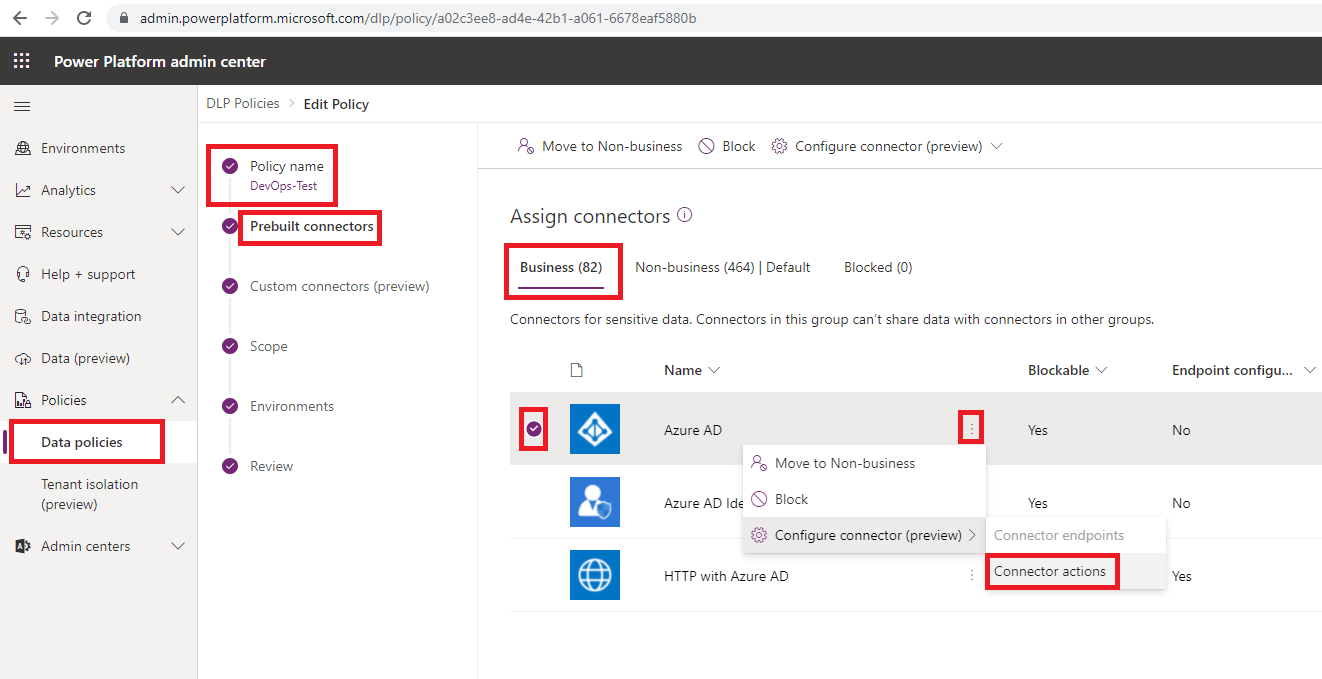
From within the Connector actions screen we can selectively choose which operations we want to enable. In the example below, we have disabled all the write operations and only allow the connector to retrieve information.
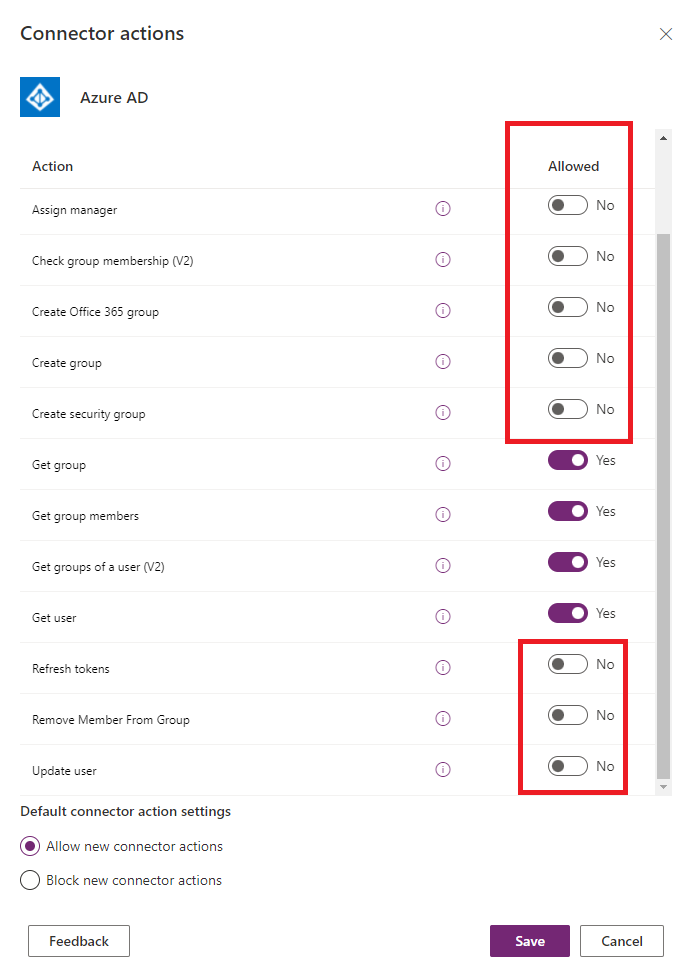
If we try to use a permitted action (Get group members), our flow will be saved and can be executed successfully.
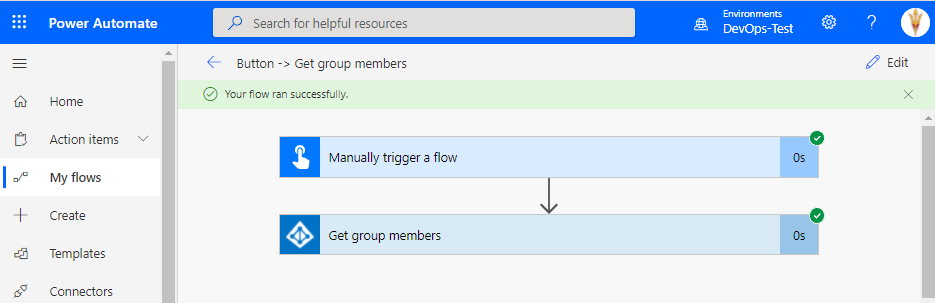
However, if we try to add an operation that writes data to Azure AD, our DLP policy will be enforced and we won’t be able to save our cloud flow until we remove the offending operation.
Conclusion
Directional DLP policies really allow administrators more control over how data is accessed within an organization. Azure AD is a great scenario where there may need to be restrictions on creating data but being able to read data is unlocked as a result.
If you would like to consume this content in video format, please check out the following YouTube video: Managing Connectors using Directional DLP policies.

