- Print
- DarkLight
- PDF
No Code Integration of Azure Key Vault with Azure Functions
- Print
- DarkLight
- PDF
Azure Key Vault is a cloud service to store secrets and sensitive information. It eliminates the need to maintain configuration files or environment variables to store sensitive information.
In this article, you will learn how to make the secrets stored in Azure Key Vault available to Azure Functions without updating the application code of the function.
Create an Azure Key Vault and a Secret
Search for Key Vault in the search box and create a Key Vault instance as follows:
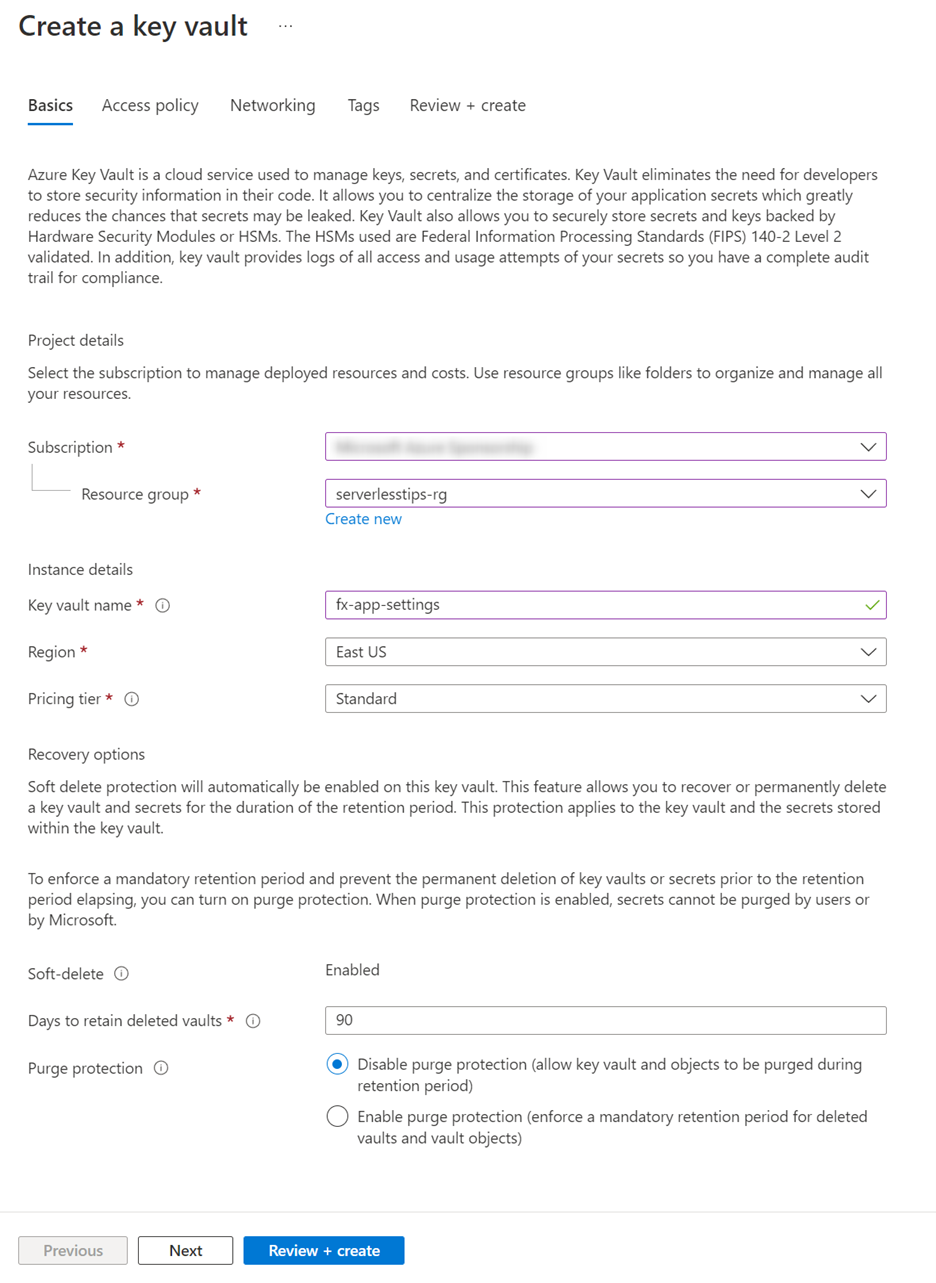
Leave the rest of the settings to their default value and click on Review + create. On the next step, click Create to submit the resource creation request.
After the instance is ready, add a secret named SuperSecretPassword to the vault with the value PasswordValue as follows:
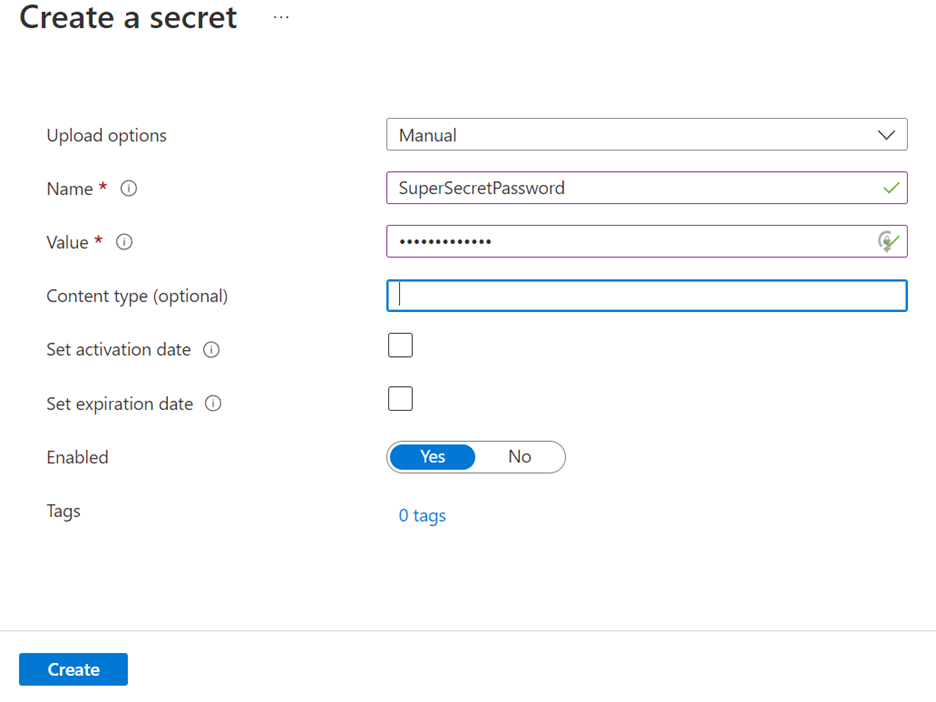
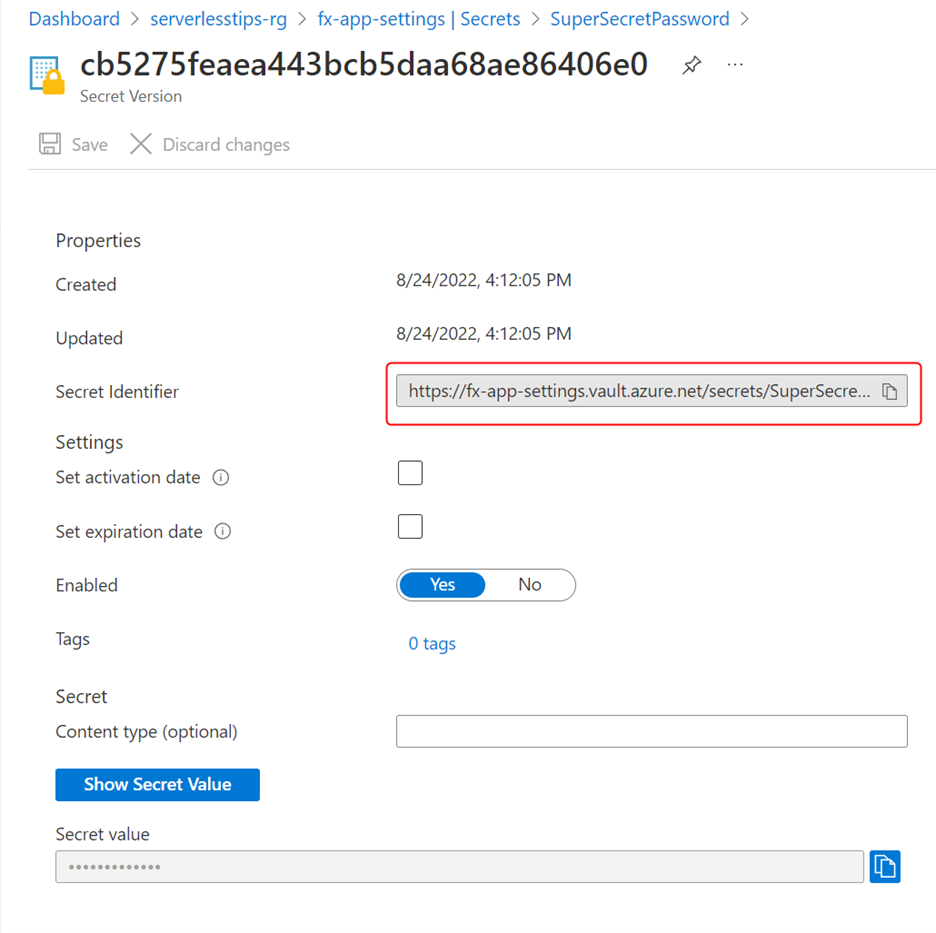
After the secret is created, click on the secret in the list of secrets available in your vault, and on the next blade, click on the current version of your secret. Copy the secret identifier value from the blade.
Create an Azure Function
Search for the term function app in the search box, and start the process of creating a Function App with the following settings:
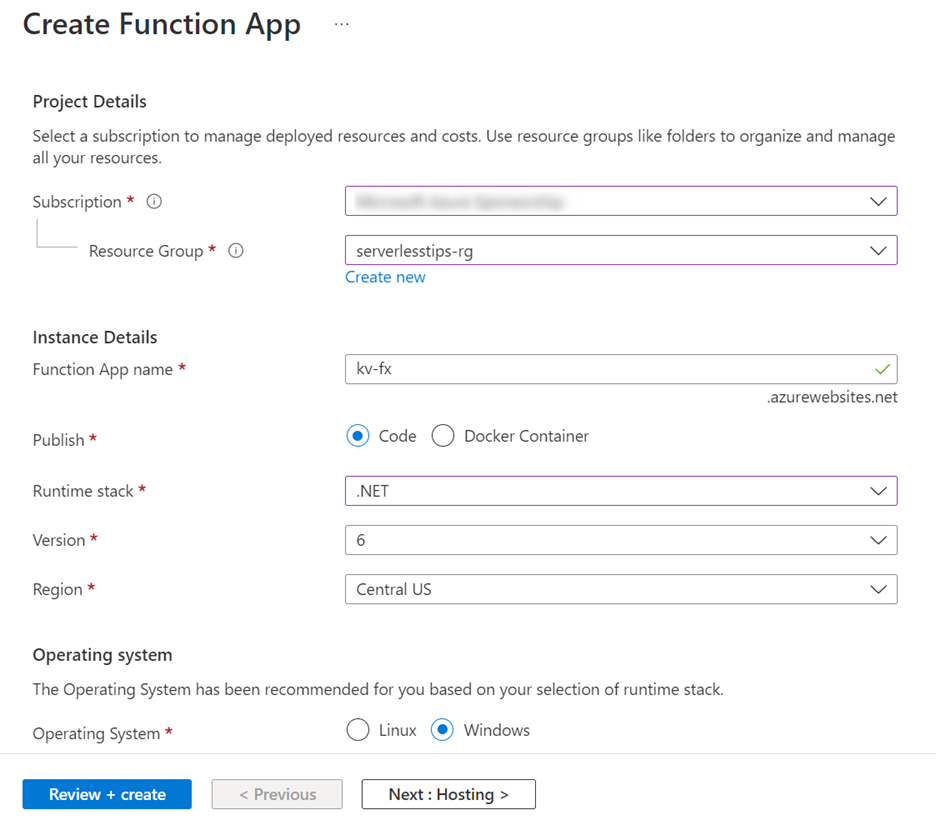
Leave the rest of the settings on their default values and click the Review + create button. On the next step, click Create to submit the resource creation request.
After the Function App is ready, click on Configuration and then click on the + New application setting button. In the following dialog, enter the name of the application setting, SuperSecretPassword, and @Microsoft.KeyVault(SecretUri=SECRET IDENTIFIER YOU COPIED) as the value.
💡Tip: The secret identifier you copied includes the version of the secret: https://<vault name>.vault.azure.net/secrets/SuperSecretPassword/<version>. You can remove the version part from the URI (the final URI should end with /) so that the identifier points to the latest value of the secret.

Add an Access Policy for Azure Key Vault
In the function app, Click on Identity and turn on the toggle for System assigned identity as follows:
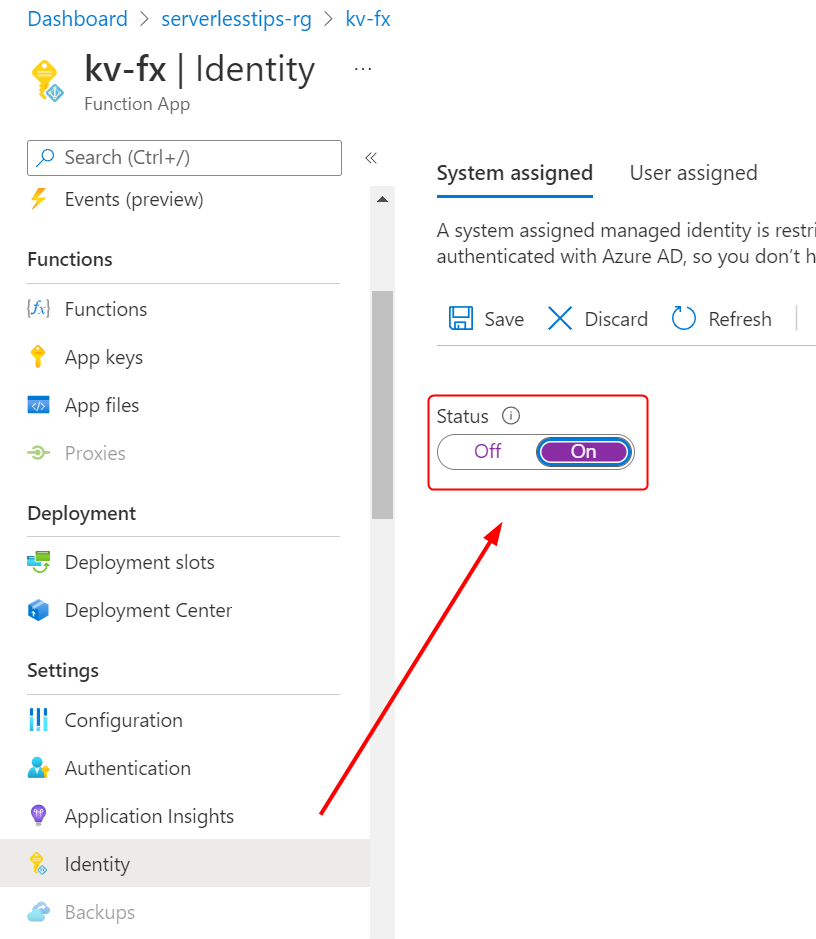
Go to Key Vault and click on Access Policies and add a new policy by clicking on the + Add Access Policy button as follows:
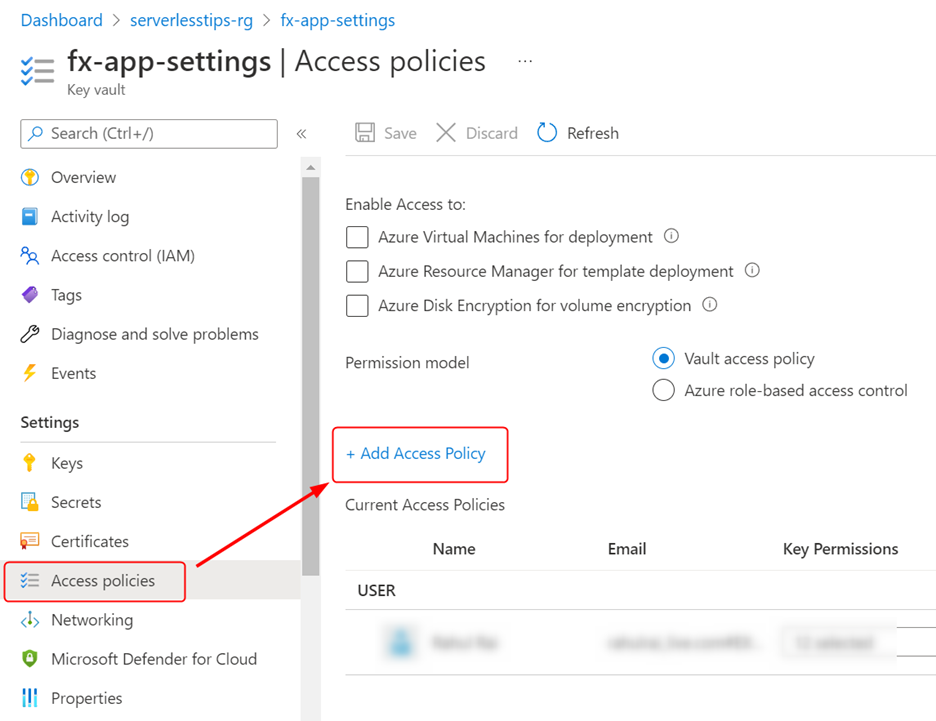
In the following dialog, grant the permission (GET) to access secrets. Select your function app as the service principal as follows:
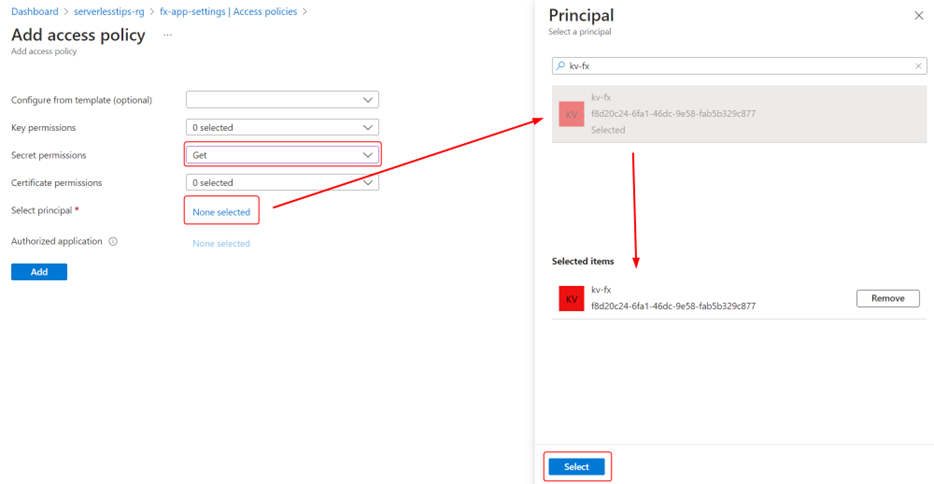
Click on Add and then Save to save the policy. Your function app can now use the Key Vault secret like any other app setting. Let’s test it now.
Testing The Function
In your function app, click on Functions and create a new HTTP trigger function as follows:
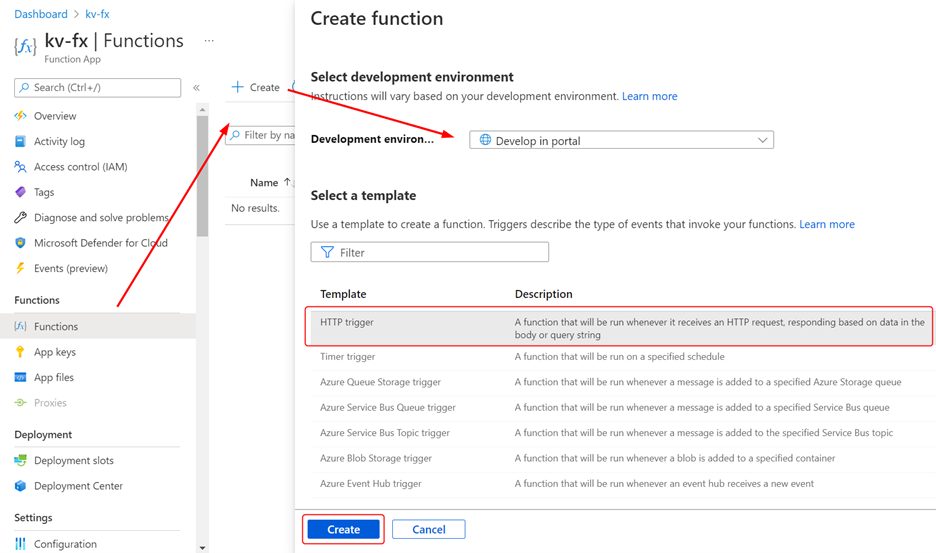
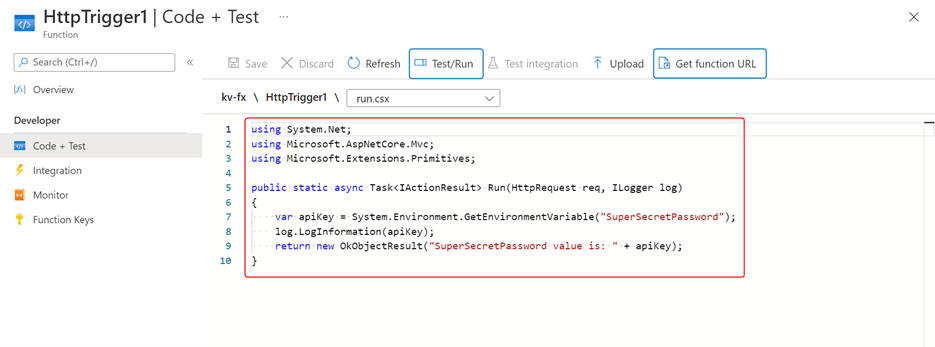
Once the function is ready, click on it from the list of functions. Click on the Code + Test button to reveal the boilerplate code. Replace the code with the following to return the value of the app setting as the response to the request to the function:
using System.Net;
using Microsoft.AspNetCore.Mvc;
using Microsoft.Extensions.Primitives;
public static async Task<IActionResult> Run(HttpRequest req, ILogger log)
{
var apiKey = System.Environment.GetEnvironmentVariable("SuperSecretPassword");
log.LogInformation(apiKey);
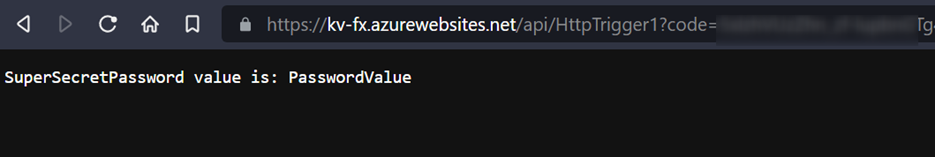
return new OkObjectResult("SuperSecretPassword value is: " + apiKey);
You can use the Test/Run button to test the function within the portal. You can also send a request to the function by copying the function URL as follows:
Here is the response from the function for a request sent to it: