- Print
- DarkLight
- PDF
Prevent Cross Tenant Connectivity in Power Platform
- Print
- DarkLight
- PDF
Protecting organizational data is very important, especially when powerful productivity tools, that are easy to use, are broadly distributed. For this reason, it is very important that administrators understand what data their users have access to.
There are many tools available that help administrators govern data access. Security roles, Environment access and Data Loss Prevention (DLP) policies are all tools that administrators can use to prevent the exfiltration of data.
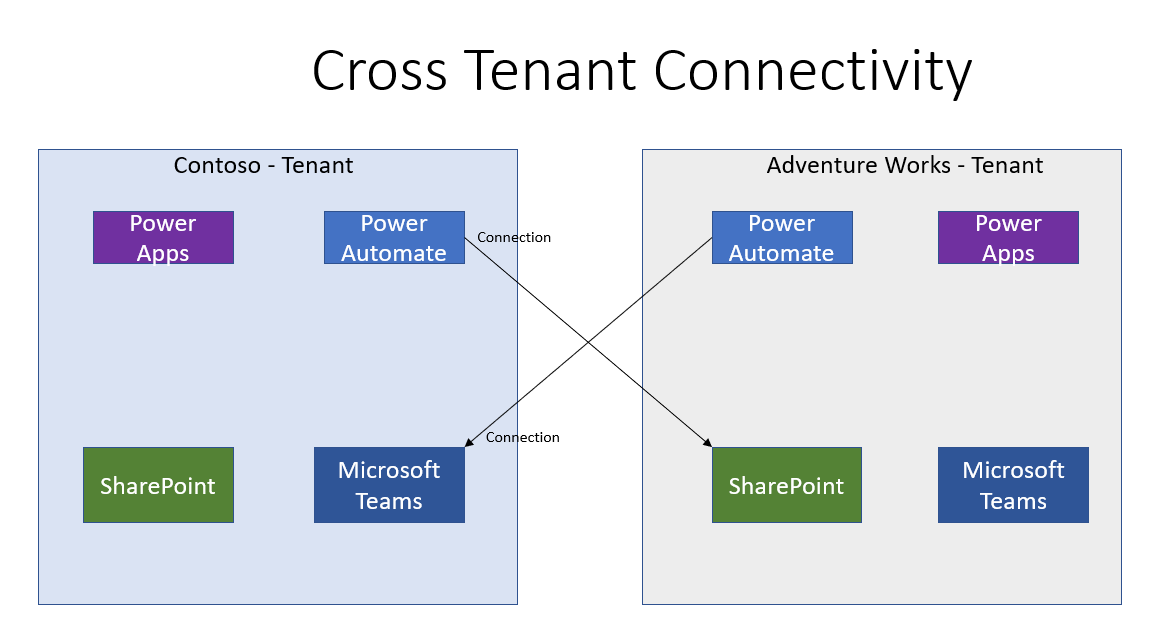
However, there is another concept that is often overlooked and that is cross tenant connectivity. What is cross tenant connectivity? Cross tenant connectivity is when you have access to accounts in two different tenants and you use these accounts to exchange data across the two tenants.
There are some scenarios where cross tenant connectivity is a good thing. This may include
- Parent – subsidiary corporate relationships: where the parent company may want to share assets with the subsidiary (or vice versa).
- Mergers and acquisitions: During a transitionary stage, it may make sense to allow cross tenant connections to aid in the migration of data.
But, outside of these types of scenarios you may not want users to be able to extract data from one tenant to another as it could be used for malicious purposes.
How does cross tenant connectivity work?
By default, a user can log into the Contoso tenant and create a cloud flow. When prompted to create a connection to use the SharePoint connector, they can establish this connection using the credentials from another tenant, such as Adventure Works. When this flow runs, it will run in the context of the Contoso user. However, when it comes to using the SharePoint connector, it will use a connection that allows for connectivity into the Adventure Works tenant. As a result, the cloud flow that is hosted in the Contoso tenant can subsequently use the data from the Adventure Works tenant in downstream actions.
The scenario that was just described also applies in the other direction. A cloud flow that was created in the Adventure Works tenant can connect to the Contoso tenant when credentials are used from that tenant when creating a connection.
How do I prevent cross tenant connectivity?
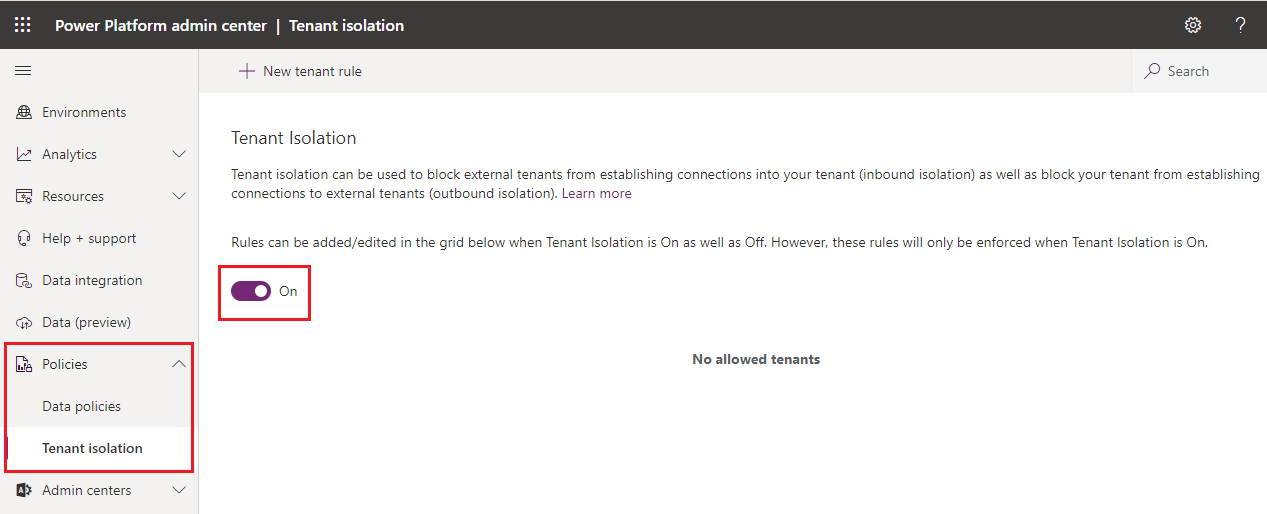
Note: if you don’t see this experience in your Admin Portal, log a support ticket with Microsoft.
By default, Tenant Isolation will be disabled. This means that you can make connections to other tenants and vice versa. To prevent this from happening, enable this setting.
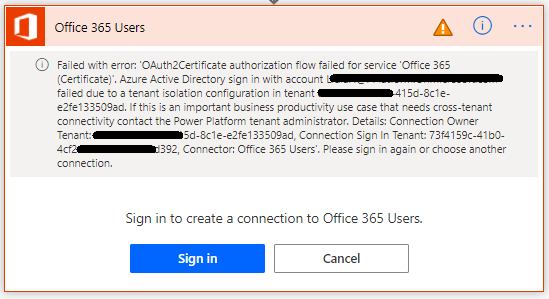
If we try to create a connection to another tenant when this setting is enabled, we will get an error message indicating that the connection cannot be made due to tenant isolation configuration.
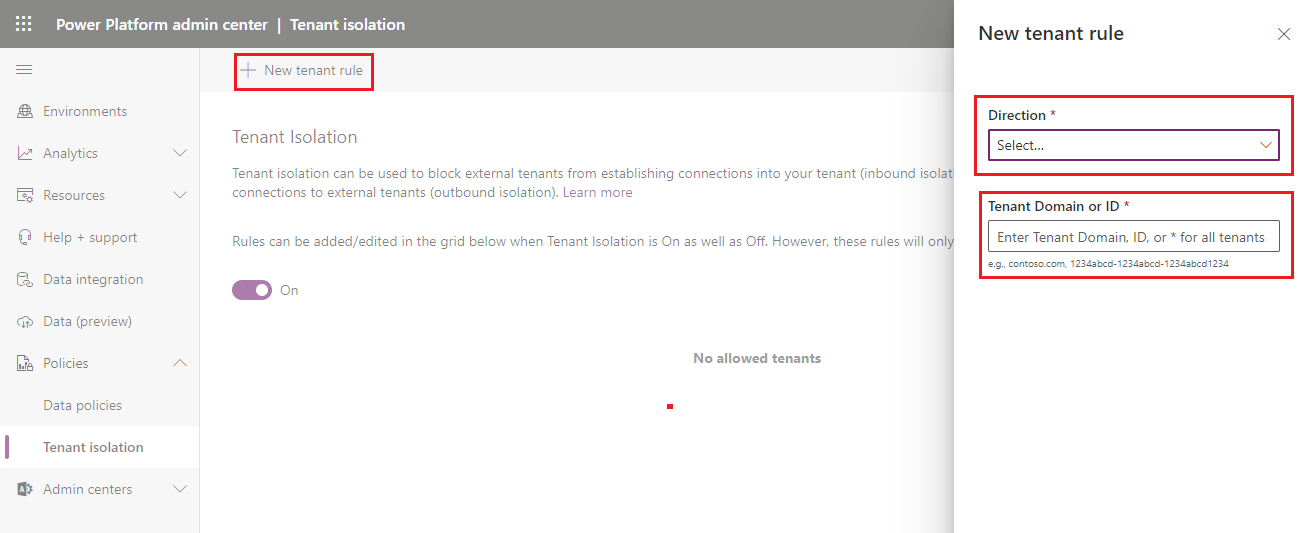
Can I create an exception?
The good news is yes. There may be situations, as described earlier in this post, where you want to enable certain tenants to participate in cross tenant connectivity. We can create inbound, outbound or inbound and outbound rules and provide the domain or tenant id. This unlocks some of those parent company-subsidiary situations without creating a broad surface area.
Conclusion
It is important to understand what your options are when it comes to governance and security so you can make an informed decision. In this post we discussed how we can prevent cross tenant connectivity from occurring when enabling tenant isolation in the Power Platform Admin center.

