- Print
- DarkLight
- PDF
Restricting Access to HTTP Trigger Endpoints using Workflow Settings
- Print
- DarkLight
- PDF
When developers publish Logic Apps that use an HTTP Trigger, there naturally are some concerns about who can call that endpoint and whether data can be exfiltrated unknowingly. While there are a couple ways to solve this, we will show the simplest, most cost effective approach that is native Azure Logic Apps. In addition, putting Azure API Management in front of Azure Logic Apps is also a viable option.
To restrict access to HTTP Trigger Endpoints, please follow the following steps:
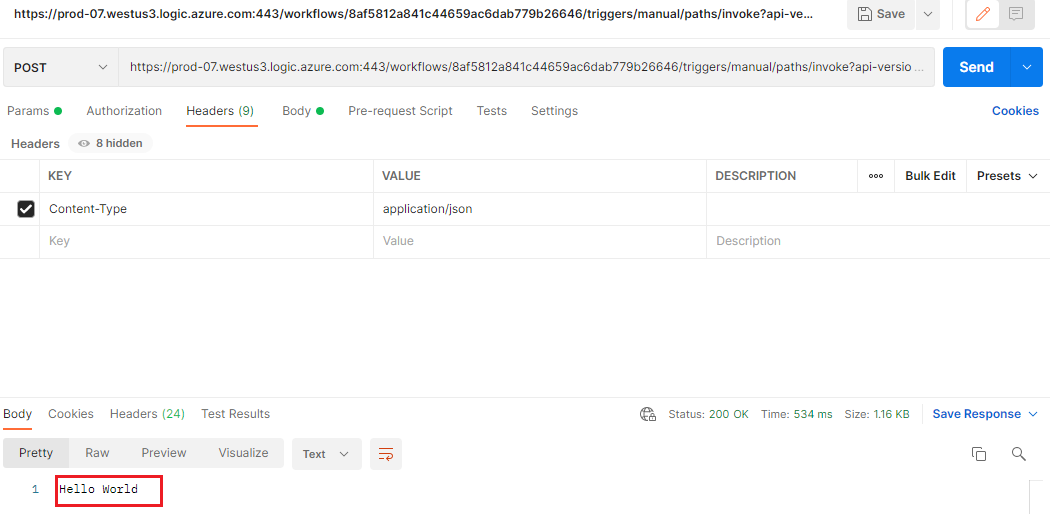
- Let’s start with a simple Request-Response Logic App that we can call from PostMan. Once our Logic App has been saved, we can copy the URL by clicking on the paper icon.
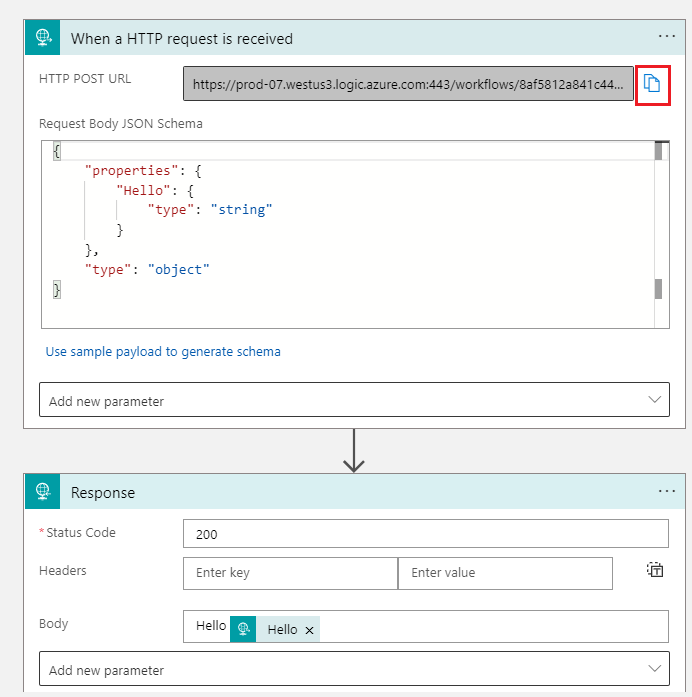
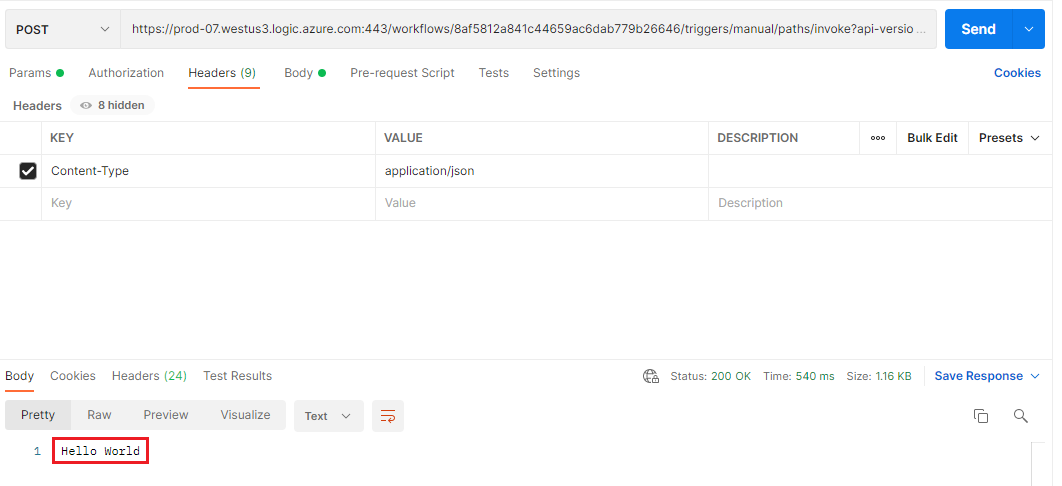
- We can call this endpoint without restrictions as long as we include our security token that is part of the URL that we copied.
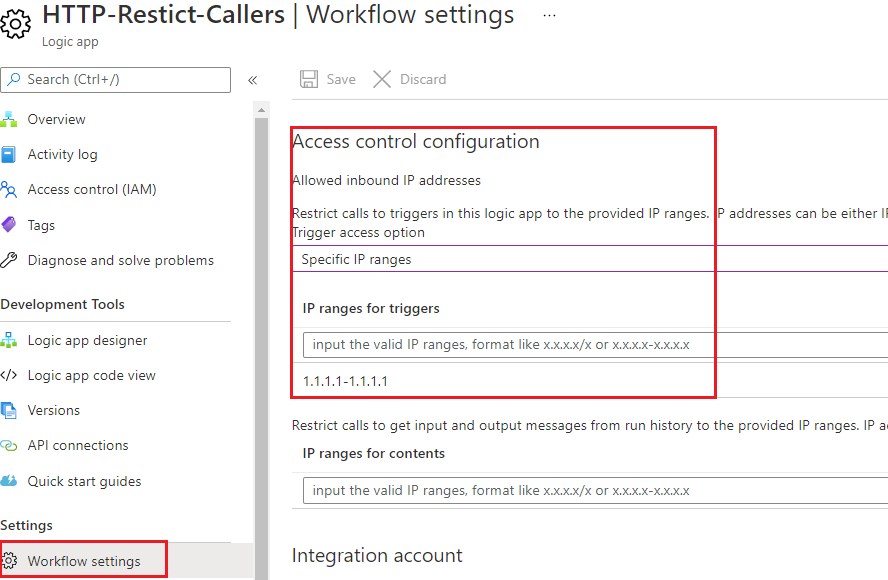
- Let’s now implement some restrictions on who can access this endpoint. We can do so by clicking on the Workflow settings link in our left navigation pane. From there, implement an IP Address range that allows for IP Addresses within this range to call our Logic App. For the purpose of this post, I will add an IP range that I don’t own so that when I call this Logic App, it should fail. Click Save to continue.
In addition, if we wanted to provide restrictions on who can see input/output telemetry we can provide IP ranges for contents.
- When we call our Logic App again from Postman, we will find that our request is blocked.
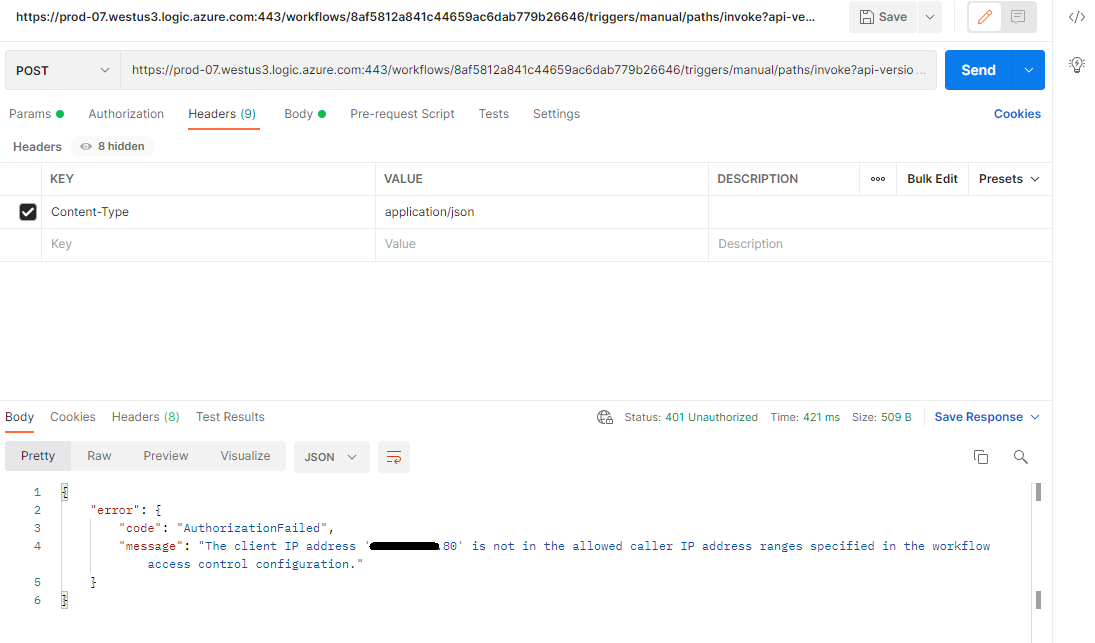
- We can now take the client IP address from this error message and add it to our permit list. When we use PostMan to call our Logic App, we will see a successful execution.
Other Considerations
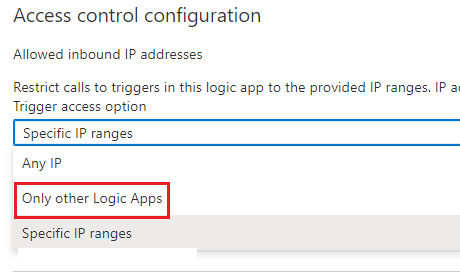
Another consideration is that when we have Logic Apps that call other Logic Apps we can specify to trust Only other Logic Apps. This allows you to have some flexibility but being less concerned about managing the exact IP addresses.
Conclusion
Regardless of your scenario, it is a good idea to restrict who can call your Logic App endpoints. Should Azure API Management not be an option, using IP restrictions within Azure Logic Apps is a good option.


