- Print
- DarkLight
- PDF
Role Based API Operation Access in APIM with Validate JWT Policy
- Print
- DarkLight
- PDF
The Azure API Management service provides an inbuilt validate jwt policy to enable Client Credentials OAuth 2.0 flow . The bare minimum validation that you can implement is to have the aud and appId claims validated to ensure that the correct client app is calling the correct API. This can be done by using the validate JWT token policy as shown below.
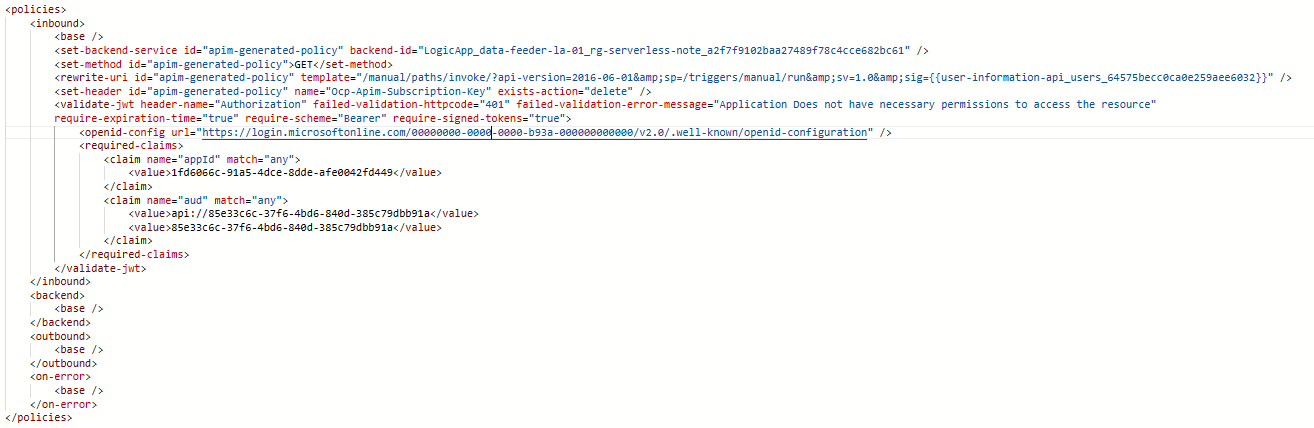
This approach is restrictive in nature. If you have CRUD operations for an API, then defining this policy on all operations will grant the consumer the CRUD rights on the API. You may want to restrict certain apps to provide only selective rights. Let’s consider that you only want to grant the Read rights to a consumer.
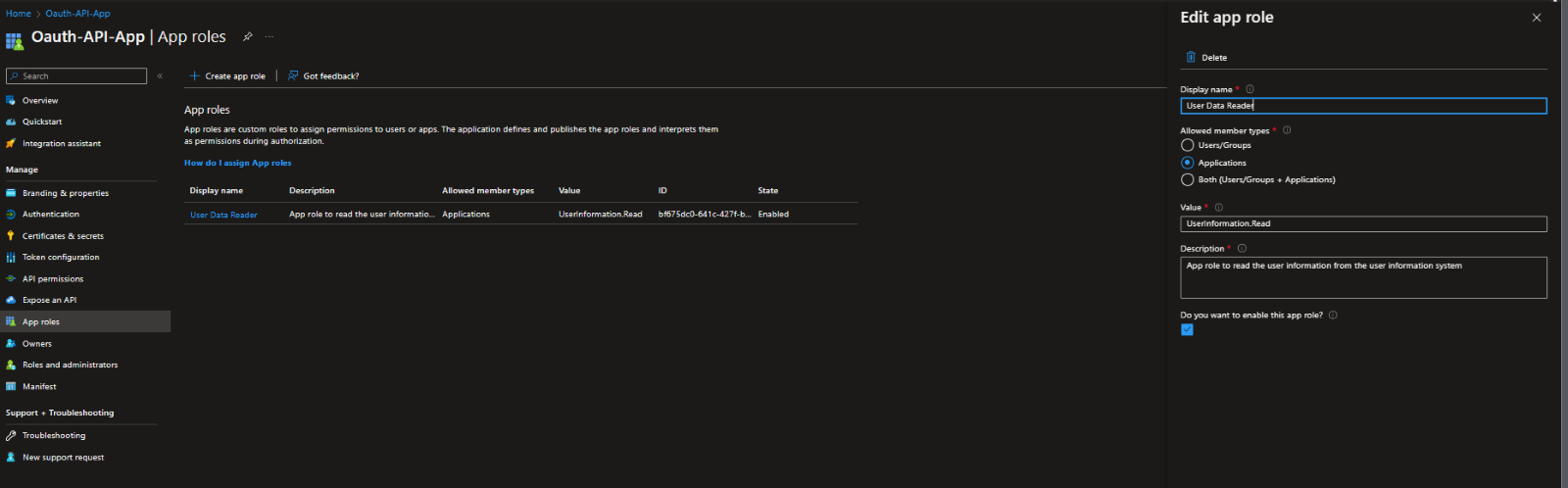
You start by defining the app roles in the app registration which represents the API being consumed. A sample is shown below
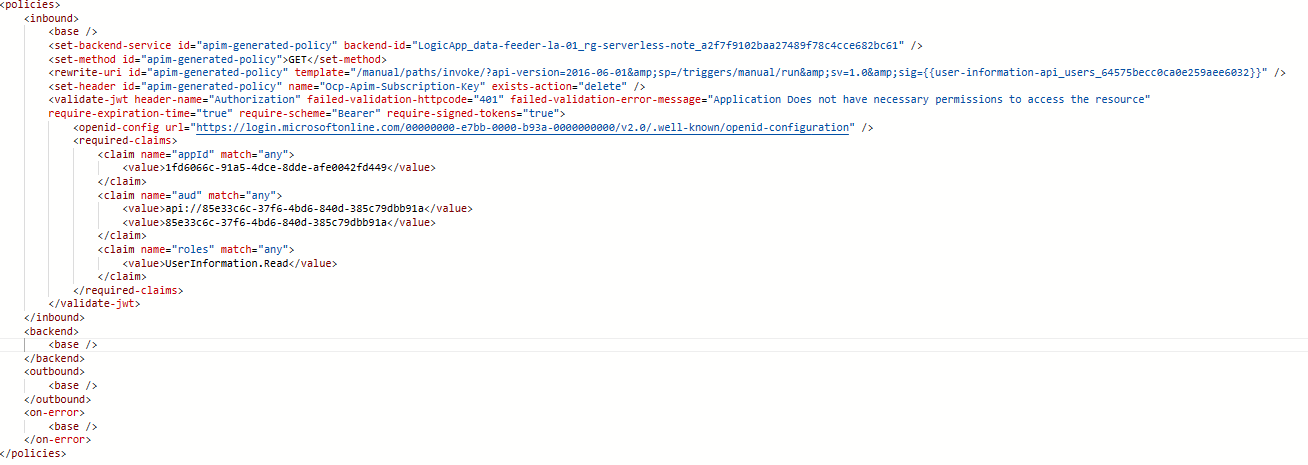
Now you can amend the validate jwt policy to check for this app permission. It can be done as shown below
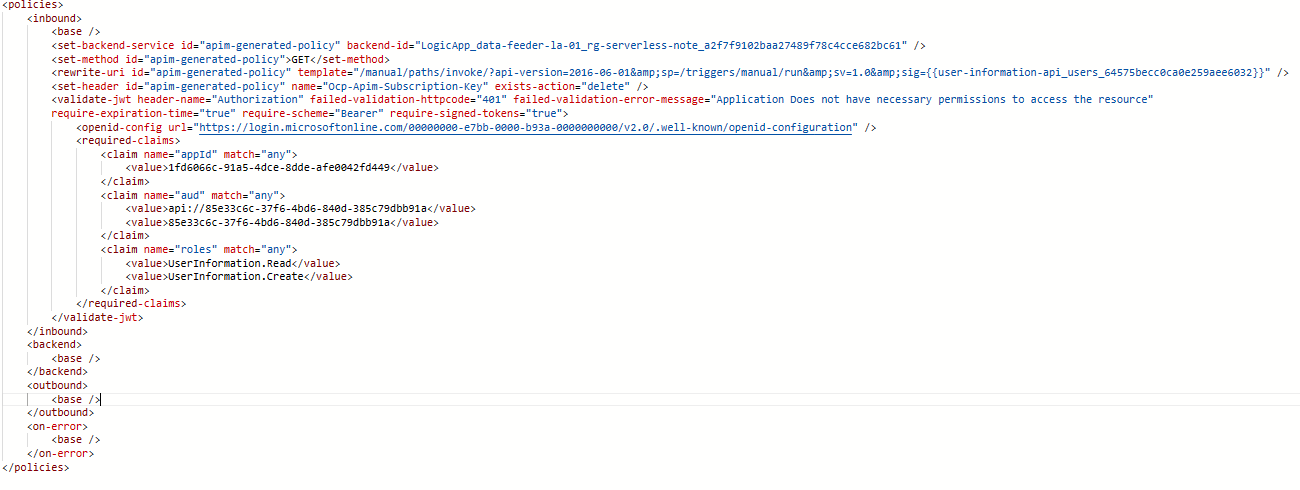
If for another application you want to give both read and create permission, you can define the jwt policy on create as follows
This way you can add role-based authorization to the different operations of the API.


