- Print
- DarkLight
- PDF
Secure Logic Apps Using API Management
- Print
- DarkLight
- PDF
Azure Logic Apps is an integration Platform as a Service (iPaaS) which runs in Microsoft’s public cloud.
For some organizations, they don’t feel this mechanism meets their needs as the URL, that includes SAS token, can be copied and used outside the organization without much governance. However, Azure Logic Apps does provide additional built-in protections by allowing for IP Address filtering.
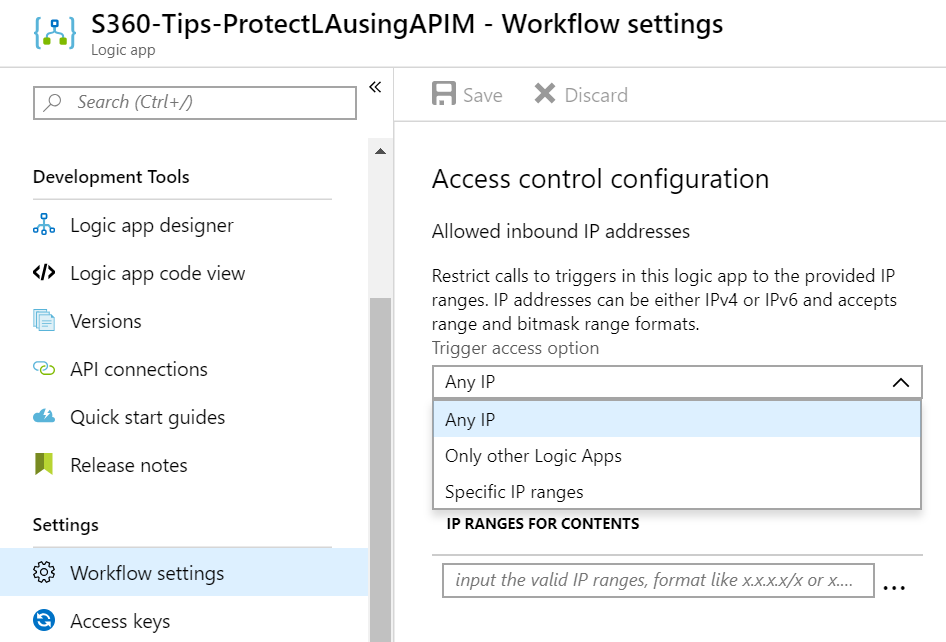
Within the Workflow settings of a logic app, there is an Access control configuration section that allows developers to apply restrictions on how their logic app can be called. For example, it can be called by any IP, only other logic apps or specific IP ranges.
Using a specific IP range will ensure that only trusted IP addresses can call a logic app.
In the event a trading partner that needs to call this logic app, their IP address(es) should be included in this configuration.
Using the out of box Access control configuration settings provide additional security measures beyond IP address filtering. But, we are also able to take advantage of additional capabilities by placing Azure API Management (APIM) in front of our Logic Apps.
The APIM team has built an experience that quickly allows developers to add new APIs to APIM, including Azure Logic Apps.
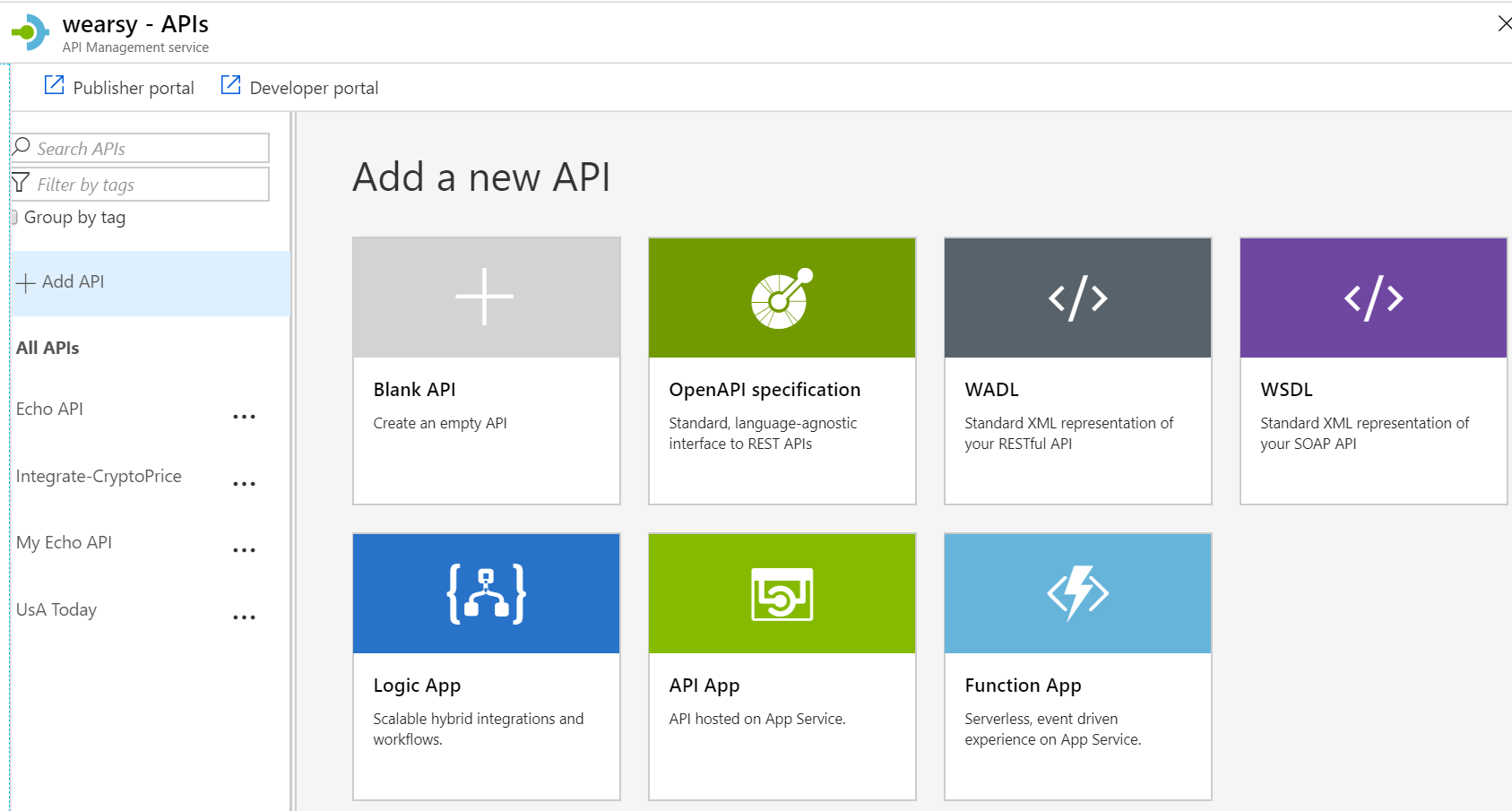
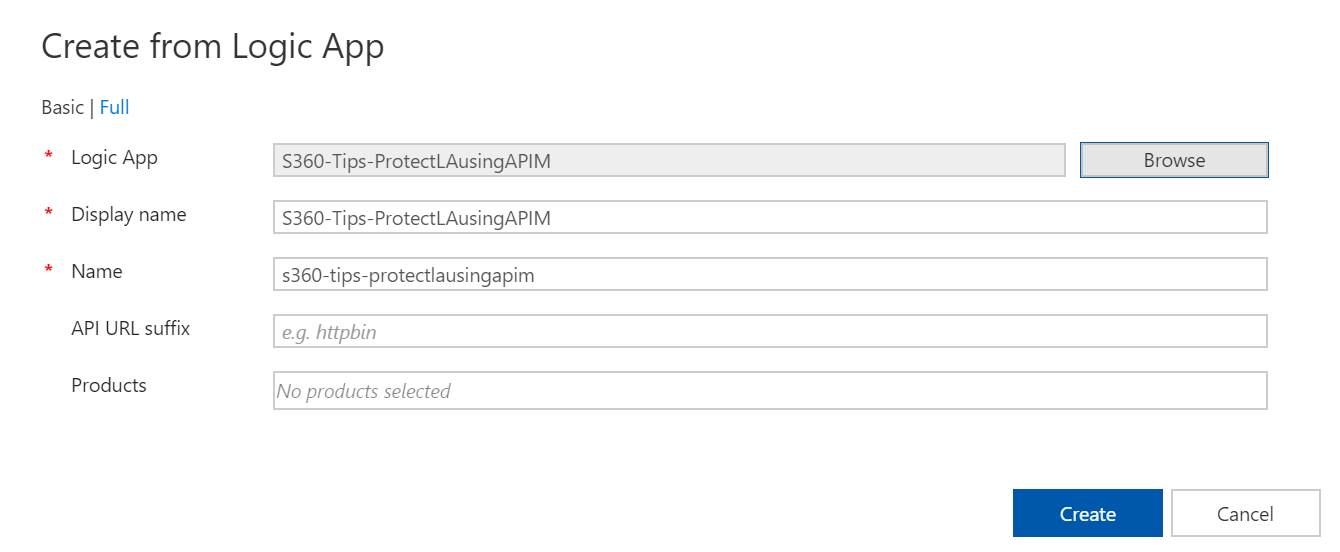
With a few clicks we can ingest our logic app configuration into APIM.
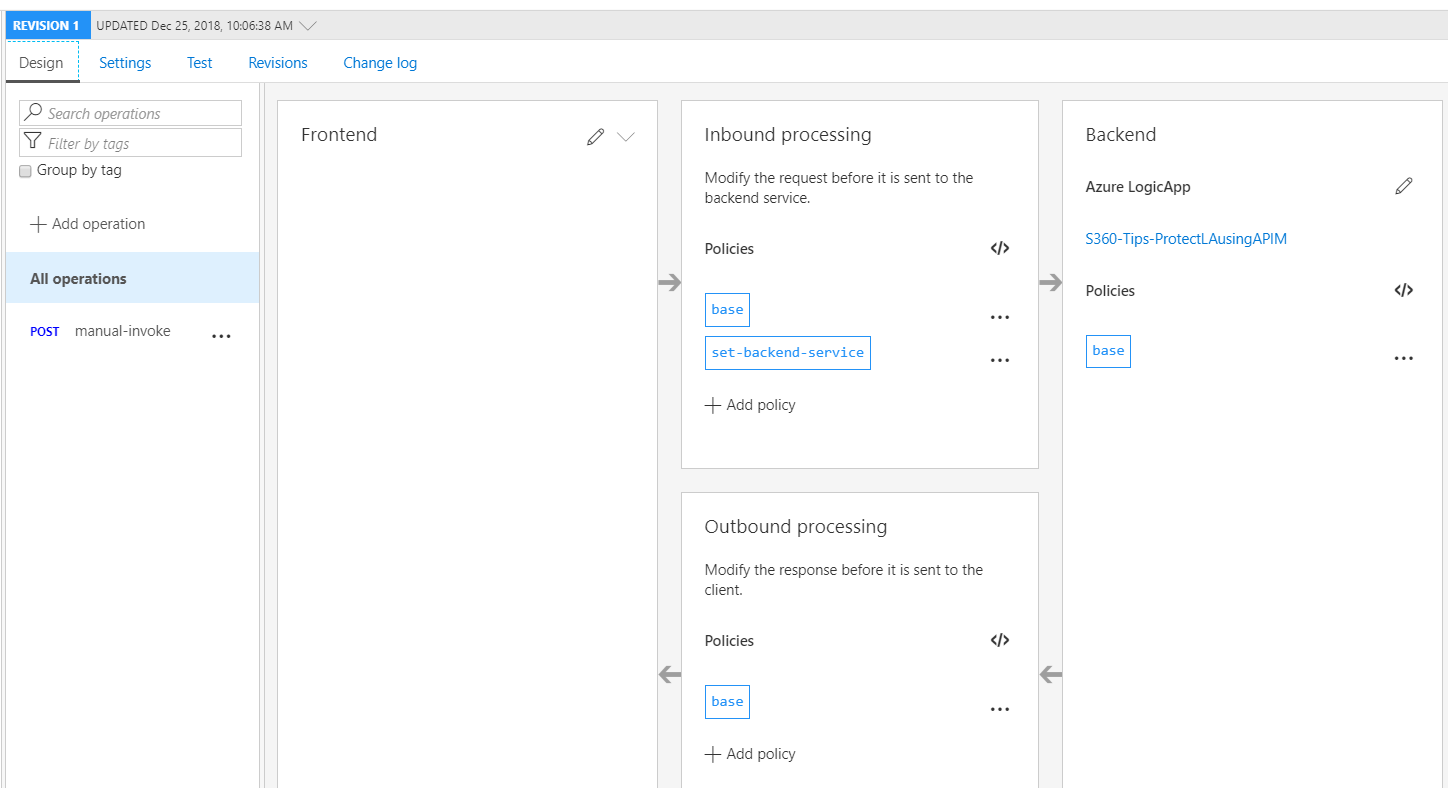
Once our logic app has been ingested, we can apply additional policies to our APIM configuration, including transformations, rate limiting, caching, IP filters and additional security schemes, beyond the SAS token that Logic Apps provide, including Basic, OAuth 2.0 and Azure Active Directory.
If you do introduce APIM to protect your logic apps, you will want to add an IP filter rule for your APIM IP address so only it can call your logic app.
Placing APIM in front of your logic app and then allowing ‘back-door’ access to your logic app defeats the purpose.
In this article, we have outlined different approaches to further secure Logic Apps when using the HTTP Request trigger. There are capabilities included in Logic Apps, but additional security and functional capabilities are leveraged when you include Azure API Management.


