- Print
- DarkLight
- PDF
Setting Headers using Custom Connector Template Policies
- Print
- DarkLight
- PDF
Custom Connectors provide an abstraction between Power Automate (or Azure Logic Apps) and an API. Since the person building the custom connector may not have access to the API that they are abstracting, you sometimes need to inject values at runtime into the request that you are making.
In the past, I have discussed how to dynamically set URLs at runtime, however I now need to be able to set a Header value. In my scenario, I have 3 operations that belong to a Custom Connector. For two of the operations, they require an Authorization header to be added. For the remaining operation, it is a login operation where I need to pass in a username/password as part of the body. I will subsequently get a token back that I can then pass into these other two operations.
Based upon the design of this API, I can’t enable authentication, on the entire customer connector, because I have some calls that are authenticated and some that are not. This means that I am better off using No Authentication for my custom connector but then include functionality to inject an Authorization header at runtime that can be used to authenticate the API call.
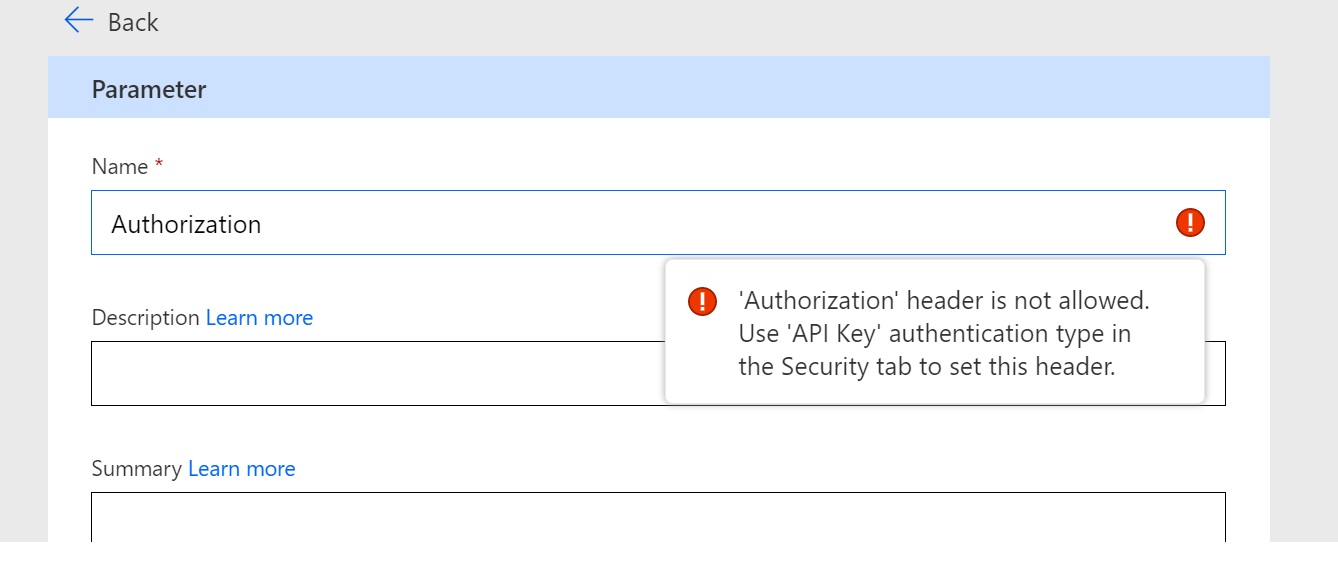
You may be thinking, for the two operations that require Authentication, why don’t you just add an Authorization Header as part of your Custom Connector design. The Custom Connector designer will not let you do it. You will end up with an error specifying: ‘Authorization’ header is not allowed. Use ‘API Key’ authentication type in the Security tab to set this header. The problem with this is that it won’t work for our scenario where we have some calls that require a header and some that don’t.
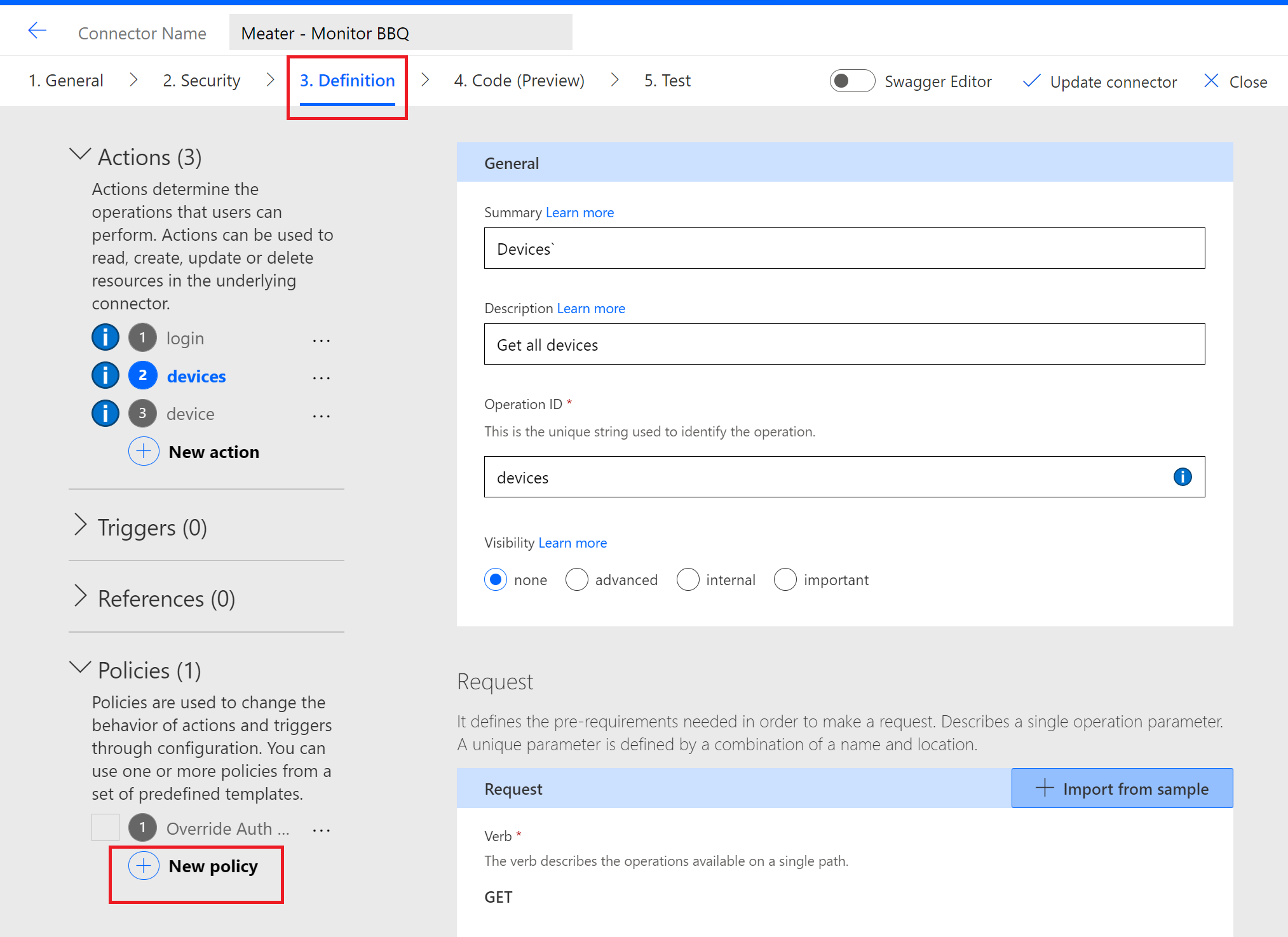
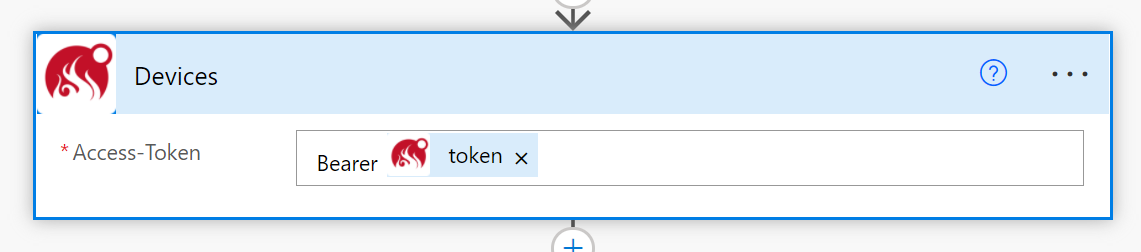
The way to work around this is to create header parameters for the purpose of authentication but call them something else like ‘Access-Token’. On your connector actions, this field will be exposed so that it can be populated. Then we will inject this value into an Authorization header as part of using a Template Policy at runtime.
To create a template policy, click on New Policy from the Definition tab.
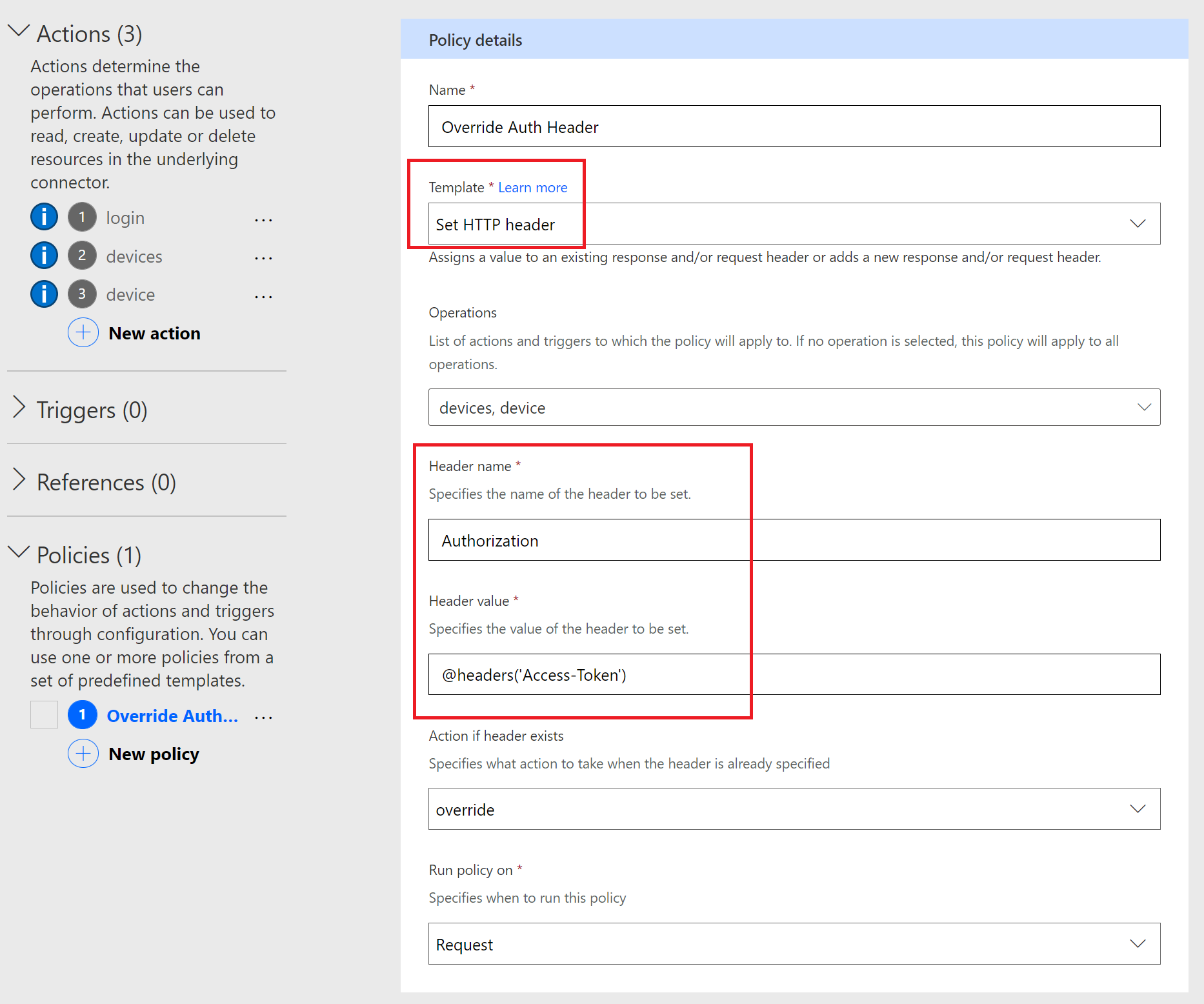
As part of our policy, we need to provide a Name, set our Template to Set HTTP Header, indicate which Operations we want this policy to be used with, the name of the Header to override, our expression of @headers('Access-Token') that will retrieve the value from our Access-Token and override our Authorization value. We also need to specify when we want this policy to be applied. In our case it will be on the Request.
We can now test our Custom Connector using the test harness or directly in a Cloud flow. When we do add our connector to a cloud flow we will see our Access-Token being requested. During runtime, this value will be used to overwrite the Authorization header and inject the value, just in time.
Conclusion
Custom Connectors are part of the extensibility capabilities found in Power Automate. Using Policy Templates, we can further customize the experience for even greater control over the API we are going to call.

