- Print
- DarkLight
- PDF
Understanding Azure API Management Authorizations
- Print
- DarkLight
- PDF
Microsoft recently introduced Azure API Management (APIM) Authorizations, which are still in preview as of 11/2022. This feature can be convenient in numerous scenarios described in the official documentation https://learn.microsoft.com/en-us/azure/api-management/authorizations-overview.
In a nutshell, APIM authorizations allow you to delegate authentication to APIM to let it authenticate against a given backend service or a given SaaS platform. It differs from managed identity in that it spans multiple identity providers (IDP), as it is not tight to Azure Active Directory.
This new feature can also leverage OAuth flows, such as the Authorization code flow, while managed identities stick to the Client Credentials Grant. I am excluding the federated credentials from the picture, which can also be used with user-assigned identities.
In technical terms, APIM Authorizations allow you to do protocol transition and token exchange to some extent. Figure 1 and Figure 2 show the different flows:
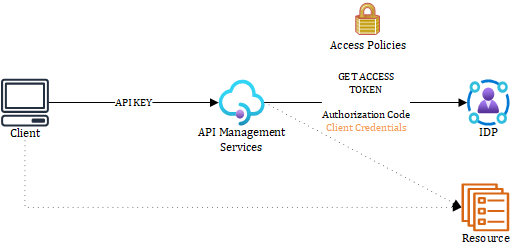
Figure 1 – API key flow
In figure 1, the client presents an API key. APIM will use the built-in get-authorization-context policy to get an access token to the target IDP using the registered authorization. APIM can use this token directly to target a given resource (SaaS application, custom backend, etc.) or return it to the caller so that the caller can interact with that resource if needed, providing APIM’s managed identity is authorized to access the authorization.
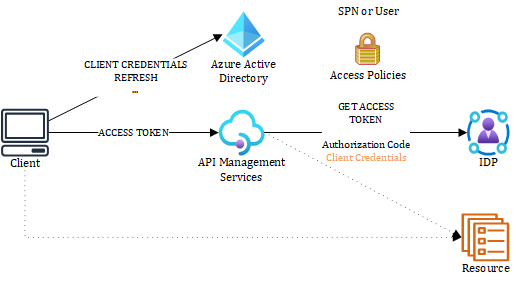
Figure 2 – Access token flow
In figure 2, the client presents an access token to APIM. This token was requested for an app using the client credentials granted.
It is for a user, or one of the authorization flows that can request tokens on behalf of a user. The app and user must be the same tenant as the APIM instance.
APIM uses the built-in get-authorization-context policy to get an access token to the target IDP using the registered authorization. APIM can use this token directly to target a given resource (SaaS application, custom backend, etc.) or return it to the caller so that the caller can interact with that resource if needed, providing the app or the user has the right to use the authorization. It allows for some token exchange scenarios.
In both cases, APIM requests tokens to the IDP using either the Authorization code flow (user context) or the Client Credential grant flow (app-only), which is not available for every IDP, hence why I colored it in orange. With APIM
Authorizations, you can use APIM as an abstraction layer between an API consumer and any resource and let APIM deal with the token request to the target IDP. The sky is the limit because it is possible to provide a generic OAuth IDP. APIM manages to refresh and access tokens, shielding you from the underlying complexity.

