- Print
- DarkLight
- PDF
Use Sensitive Text to Protect Passwords in Power Automate Desktop
- Print
- DarkLight
- PDF
Integrated authentication, like Windows Authentication, simplifies accessing both web and desktop actions without the need to explicitly provide a username and password. However, many RPA solutions involve applications that may not support integrated authentication and a username and password need to be supplied.
One thing we want to avoid is having our credentials/secrets leaked into our logs (run history). To address this need, Microsoft has introduced a new data type in Power Automate Desktop called Sensitive text.
To use Sensitive text we need to create an input within Power Automate Desktop.
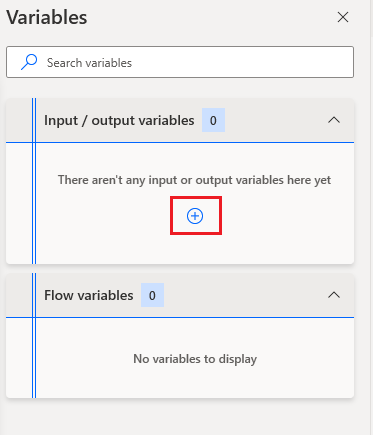
We then need to select Sensitive text from the Data type dropdown. We also need to provide Variable and External names. This allows us to easily identify our input within Power Automate Desktop and within our Cloud Flow.
We can now use this value downstream in other actions such as when opening a password protected Excel spreadsheet.
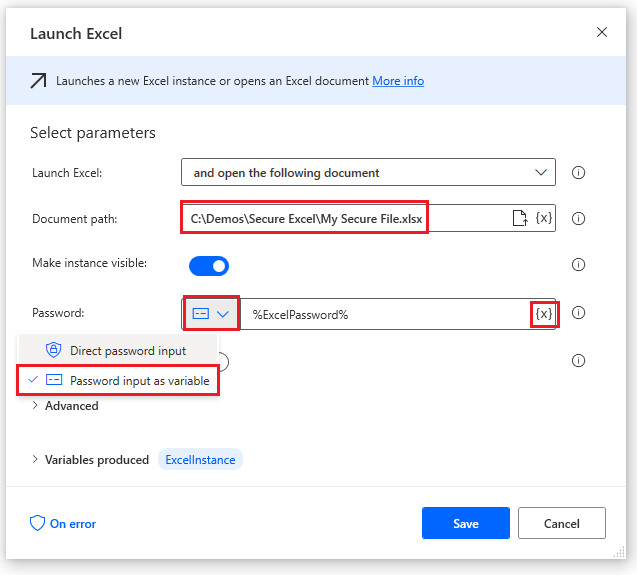
To open an Excel spreadsheet, we need to use the Launch Excel and select Password input as variable. This allows us to select the input value that we previously created.
We can now create a Cloud flow and add a Run a flow built with Power Automate Desktop action. We will provide our credentials in here.
Note: For additional security, you can store your credentials in Azure Key Vault and then pass them into this action using Secure Inputs/Secure Outputs as outlined in the following steps.
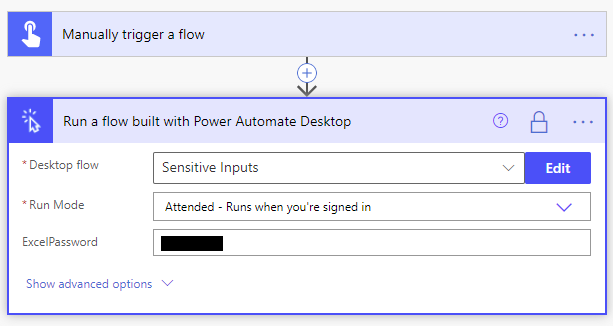
To ensure our credentials are not leaked from our Cloud flow, we can enable Secure Inputs/Outputs from the action’s Settings.
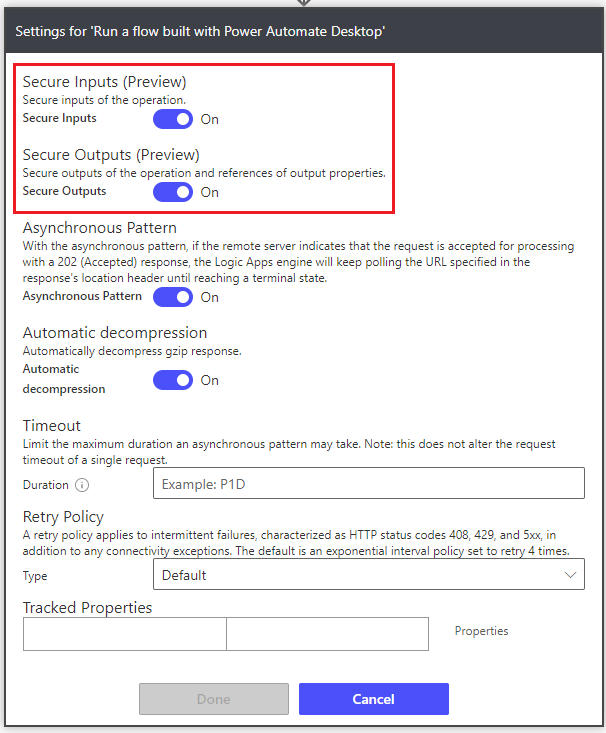
This will ensure when we run our flow that our password is not leaked into our run history logs from our Cloud flow.
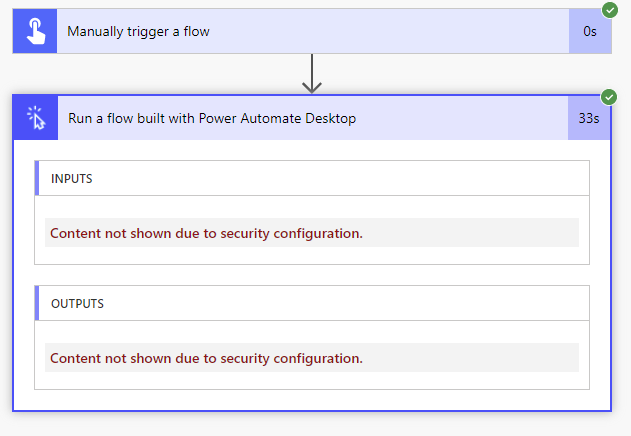
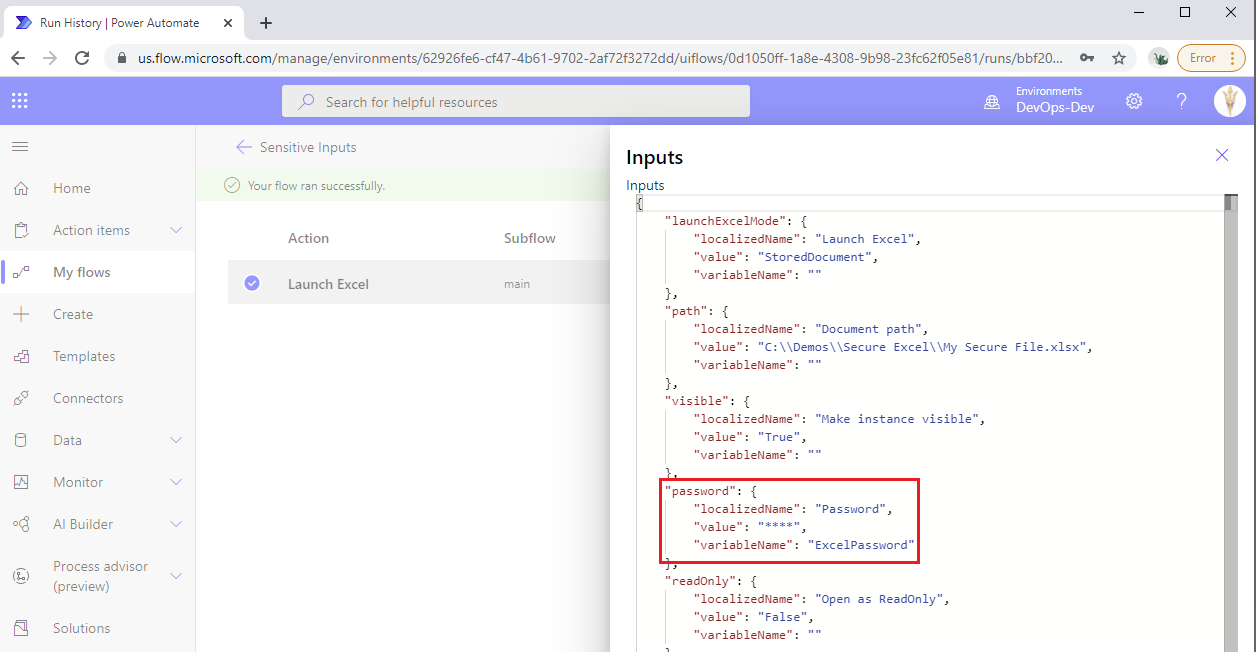
If we look at the logs for our Desktop flow, we will discover that our password has been obfuscated.
Conclusion
Microsoft recently introduced Sensitive text in Power Automate Desktop. In this post we covered how to use this feature to avoid credentials from leaking into our logs.

