- Print
- DarkLight
- PDF
Azure Storage Account: Using Azure AD over SAS to secure access to your data
- Print
- DarkLight
- PDF
When securing access to data stored in an Azure Storage Account, we used to rely on Shared Access Signatures (SAS), which defines in a granular way. It explains what resources (e.g., blobs) an individual can have access to, what permissions they have on these resources (e.g., read-only or edit), and for how long (i.e., when would that access be revoked).
When you set up a SAS token for a resource in your Storage Account, the URI will look like this (with the highlighted part representing the SAS token):
https://streaming2.blob.core.windows.net/demo2/video.mp4?sp=r&st=2022-06-10T19:02:01Z&se=2022-06-11T03:02:01Z&spr=https&sv=2021-06-08&sr=b&sig=Skyaa4iIWErBqSTsPRVTjVHpbJZ0UPUB4xZ%2Fv6KeoAk%3D
Although SAS is way better than sharing your access keys with someone else, which would instead provide access to your entire Storage Account.
However, I would recommend that you instead rely on Azure AD accounts to manage access to your Storage Account data.
So, when you create a new storage account, you can select whether you want to enforce Azure AD authentication or allow Storage Account key access (and, hence, Shared Access Signature):
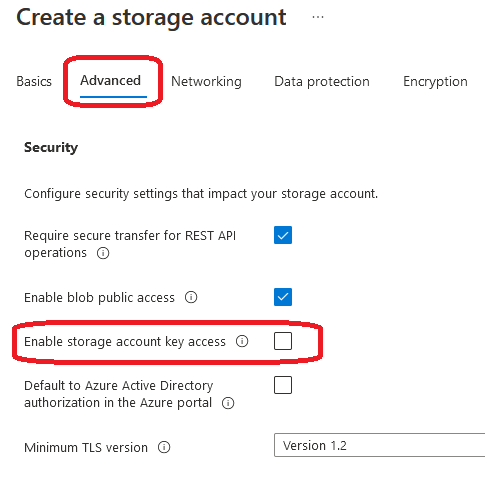
Suppose you already have an existing Storage Account. In that case, you can switch from Azure AD authentication to Access keys (and Shared Access Signatures) back and forth by enabling or disabling the appropriate setting in the “Configuration” section of your Storage Account:
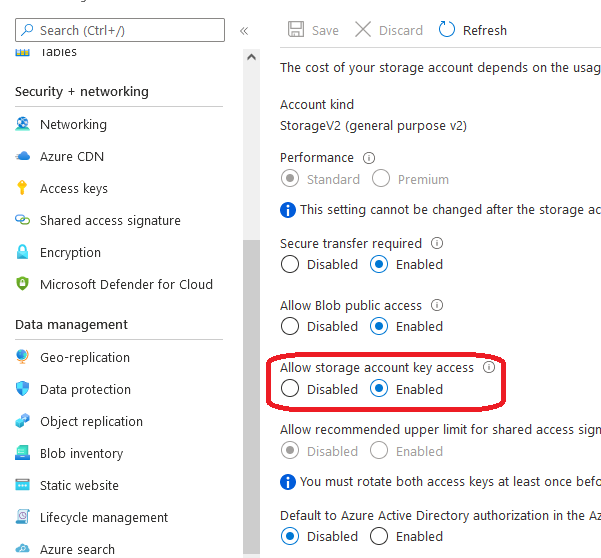
Thus, to use Azure AD roles rather than SAS tokens to manage access to data in the blob storage, you’ll need to disable storage account key access.
Then, you’ll need to assign one of the built-in roles for working with data. Here’s the list of these built-in roles:
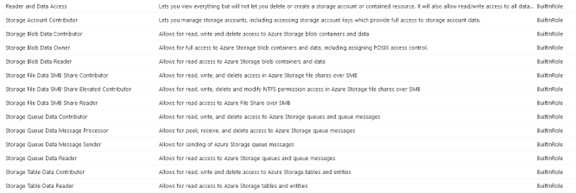
For example, we can assign the “Storage Blob Data Reader” to an Azure AD identity to allow it to read data from the blob storage. We can also give that identity with the “Storage Blob Data Contributor” role so it can read, write, and delete data from the blob storage.
To sum it up: Leveraging Azure AD roles rather than SAS tokens is the recommended approach to allowing and controlling access to the data in your Azure Storage Account instances.

