- Print
- DarkLight
- PDF
Using Configure Endpoints in DLP Policies
- Print
- DarkLight
- PDF
The governance capabilities in the Power Platform continue to evolve. We have previously discussed how we can impose directional DLP where we can restrict which way data can move (read vs write). In this post we are going to extend our governance capabilities by introducing the ability to filter URI/Host information for select connectors.
Example
Let’s take an example to illustrate the opportunity here. For many organizations, they want to block, or restrict, the HTTP connector. The reason for this is the HTTP connector unlocks accessing an unlimited amount of endpoints. This ability makes administrators nervous. However, there may be some valid business scenarios that need to be unlocked by using the HTTP connector. The Configure Endpoints capability addresses these requirements. Administrators can enable specific endpoints that are sanctioned by the organization, however all remaining end points can be blocked
Connector support
Not all connectors support this feature. As of this writing, the following connectors are supported:
• SQL Server
• Dataverse
• Azure Blob Storage
• SMTP
• HTTP with Azure AD, HTTP Webhook, and HTTP connectors
Please refer to this link to track connector support for this feature.
Solution
Let’s say that we want to allow the HTTP connector to connect to a company API that has a URL of https://biztalkbootcampkw.azure-api.net/order but all other URLs should be blocked. We can update our DLP policy to allow this.
As an administrator, we can access DLP policies from the Power Platform Admin Center and then clicking on Data policies, selecting our policy and then clicking on Prebuilt connectors.
Note: this assumes you have an existing policy in place that you want to update.
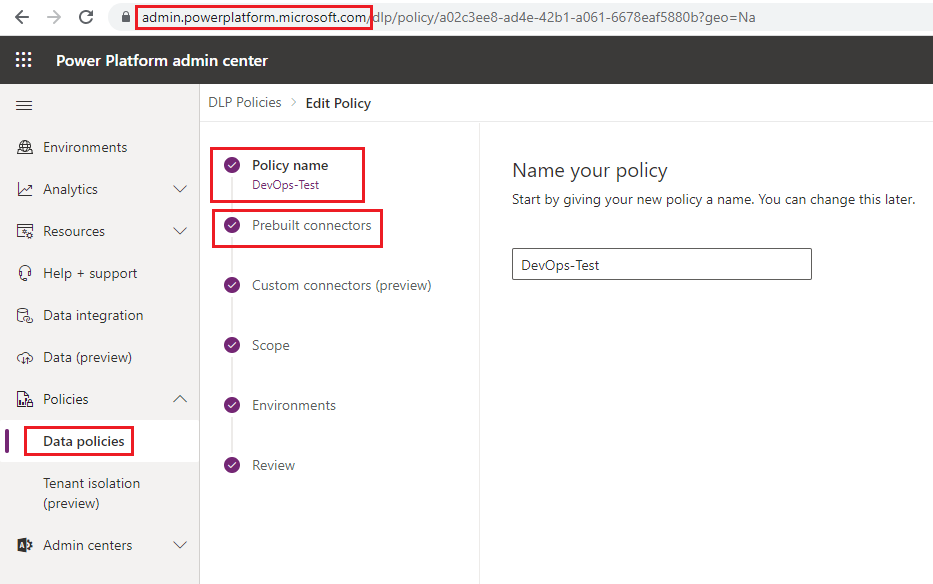
Once we are in the Prebuilt connectors experience, we need to find our connector in one of the 3 data groups. For my policy, my connector was in my Business data group. Once I have found my connector, I can select it and then click on the ellipses (…). From there, a menu will appear that allows me to click on Configure connector (preview) – Connector endpoints.
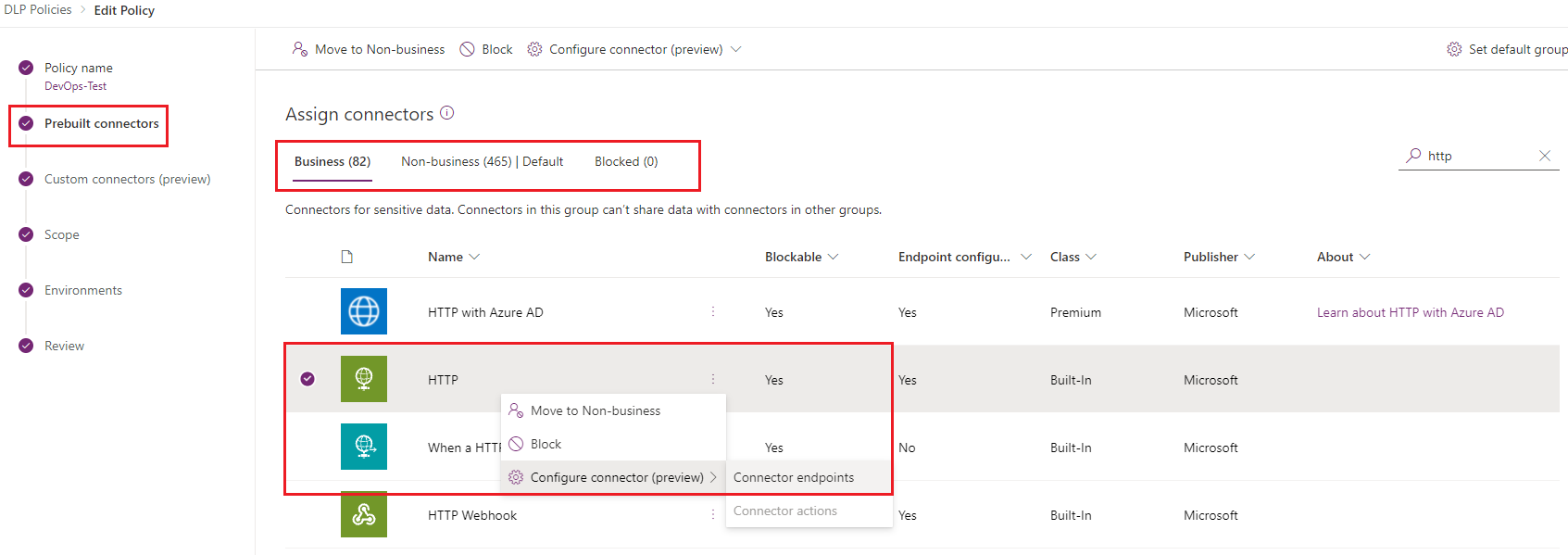
We can now establish our rules for the HTTP connector. It is important to understand how this section works. We have 2 different actions that can be set including Allow and Deny. In our scenario, we want to allow our API address of https://biztalkbootcampkw.azure-api.net* as that is a permitted URL for our organization. As a result, we want this to be in the #1 position.
Next, we want to Deny all other addresses so we will create a 2nd rule and set Action to Deny. For this particular Endpoint address, we will set the Endpoint to * meaning all other addresses.
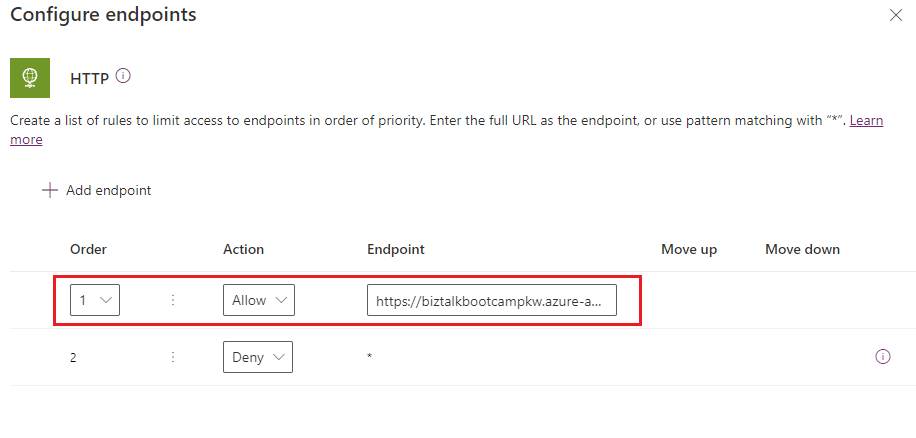
At this point we can save our DLP policy and exit the admin experience.
Maker experience
If we go into the Power Automate portal, we can create a new cloud flow and include the HTTP action. For our initial test, we will go ahead and configure our HTTP action to use our permitted URL. As you can see, we can save this cloud flow without any issue and can successfully run it.
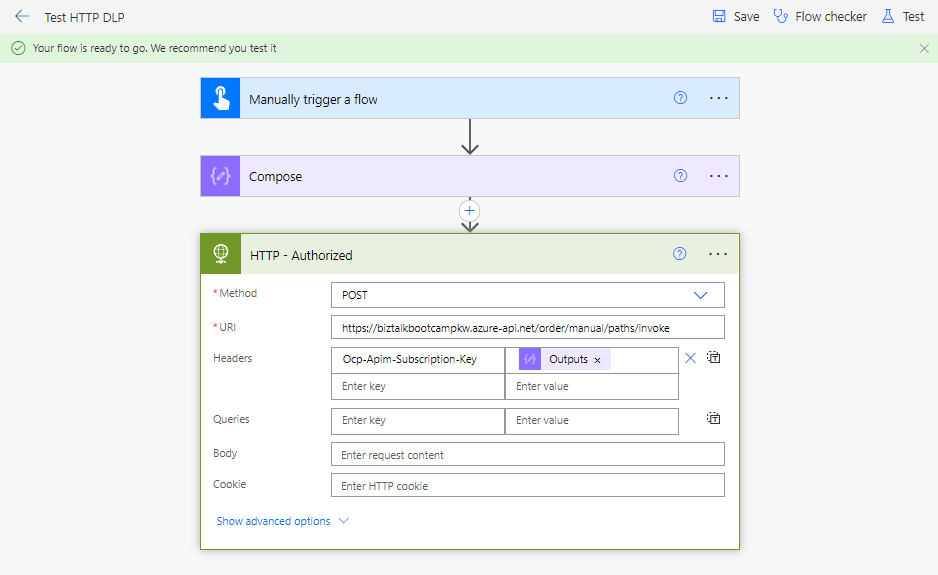
Now, let’s go ahead and add another URL that doesn’t include our permitted URL. In this case we will get an error when we try to save our cloud flow indicating that we have violated a DLP policy.
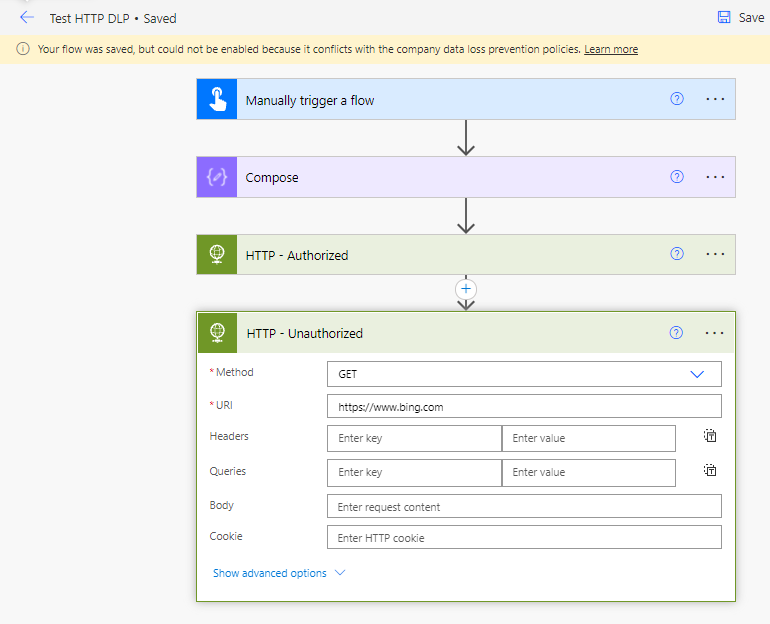
Conclusion
In this post we discussed another layer that should be included in each organization’s governance strategy. Using the Configure Endpoints feature reduces the risk that a particular connector may introduce, by only allowing specific endpoints that are approved by an organization’s administrator.
If you would like to consume this content in video format, please view the following YouTube video: Using Configure Endpoints in DLP Policies.

