- Print
- DarkLight
- PDF
Using Customer-Managed Keys for Encrypting Azure Storage Account
- Print
- DarkLight
- PDF
Customer-managed keys for Azure Storage allow you to manage the encryption keys used to encrypt your data at rest. This means you have control over the key to encrypt and decrypt your data stored in Azure Storage. You can use either Azure Key Vault or Azure to store your keys. You can create and store your keys in the critical vault, manage HSM, or use the Azure Key Vault APIs to generate the encryption keys.
In this article, you will learn to create a customer-managed storage encryption key and use it to operate with Azure Storage using a .NET application.
Follow the quickstart guides for Azure Storage and Azure Key Vault to create your respective accounts. Once the accounts are ready, navigate to your storage account and select the "Encryption" option. In the "Encryption selection" section, set the type to "Customer-managed keys" and use the "Select a key vault and key" option to select the Key Vault where the encryption key is stored as follows:
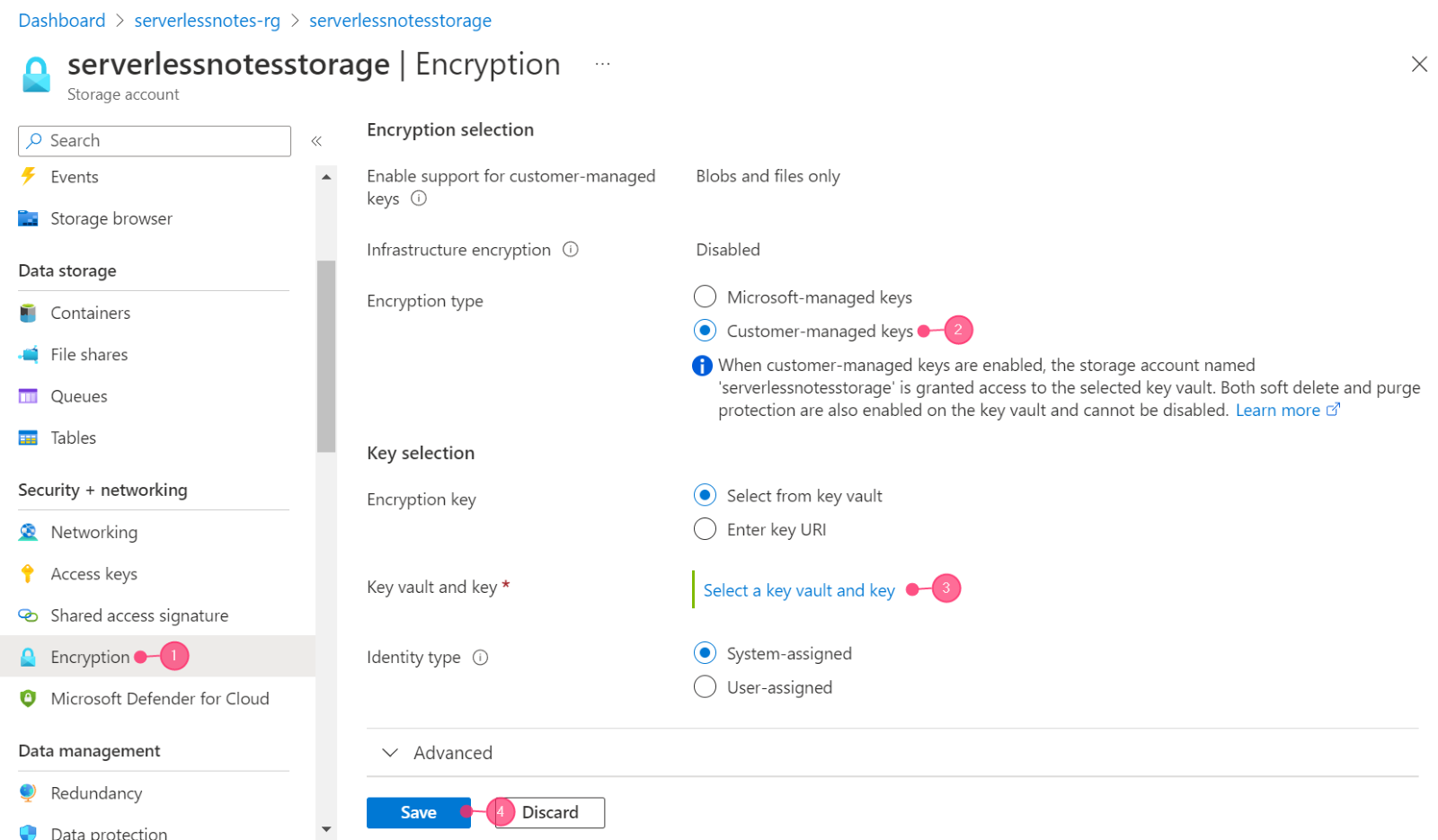
Fig1.Set the type of encryption
In the wizard’s next step, choose the subscription for your Key Vault, your Key Vault name, and the critical name where your encryption key is stored. If you wish to create a new key from this step, click the "Create new key" option. Next, click the "Select" button to return to the previous wizard. Finally, click "Save" on the previous wizard to save your preferences.
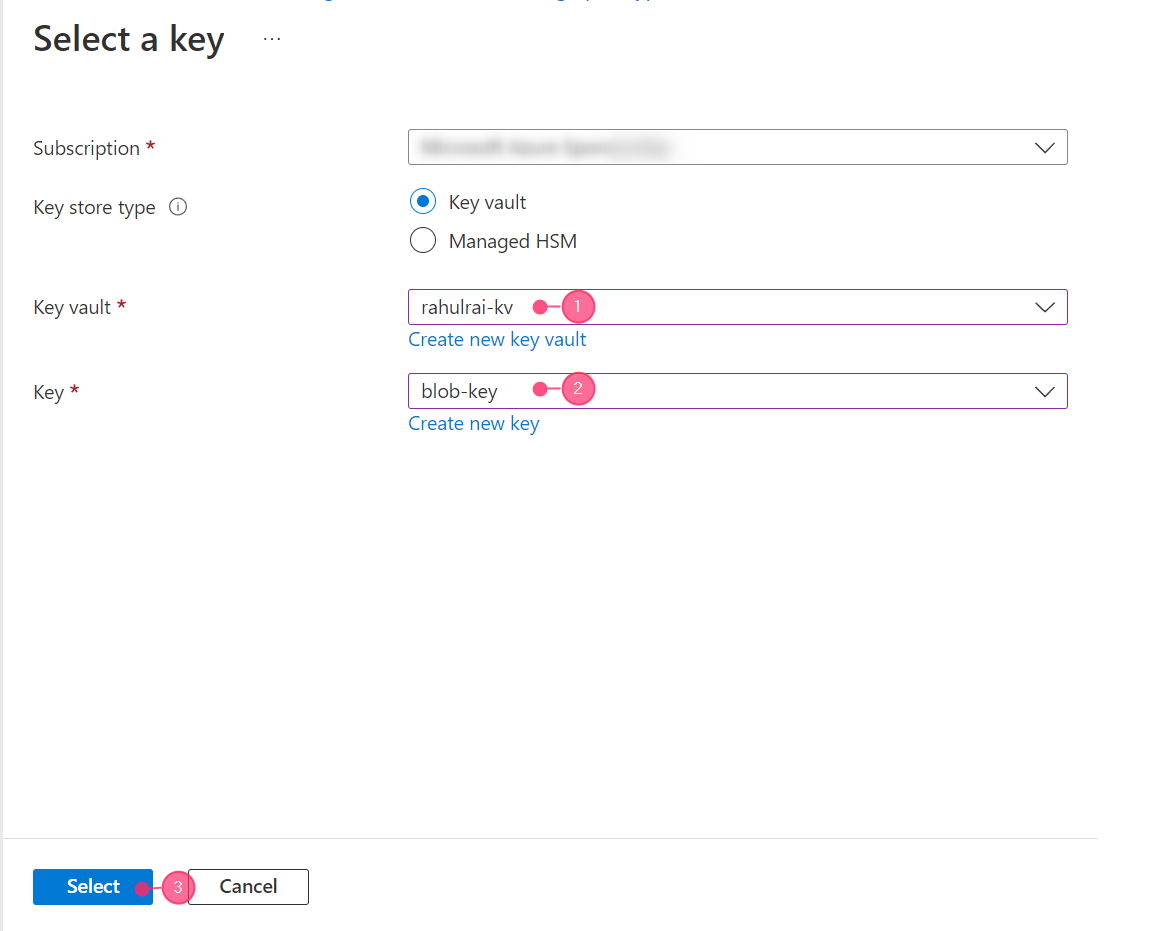
Fig2.Select the encryption key.
Create a .NET Core console application and install the following NuGet packages in it:
- Azure.Identity
- Azure.Security.KeyVault.Keys
- Azure.Storage.Blobs
Use the following code to create a BlobServiceClient object that uses a customer-managed key from Azure Key Vault to encrypt and decrypt data in the specified container. Make sure the placeholders are replaced with actual values.
using Azure.Security.KeyVault.Keys;
using Azure.Storage.Blobs;
using Azure.Storage.Blobs.Models;
string keyVaultUri = "https://mykeyvault.vault.azure.net";
string storageAccountName = "mystorageaccount";
string containerName = "mycontainer";
var credential = new DefaultAzureCredential();
var keyClient = new KeyClient(new Uri(keyVaultUri), credential);
KeyVaultKey key = keyClient.GetKey("mykey");
var blobServiceClient = new BlobServiceClient(
new Uri($"https://{storageAccountName}.blob.core.windows.net"),
credential,
new BlobClientOptions() { CustomerProvidedKey = new
CustomerProvidedKey(key.Key.N) }
);
var containerClient = blobServiceClient.GetBlobContainerClient(containerName);

