- Print
- DarkLight
- PDF
Azure Automation Account: Using Managed Identities over RunAs accounts for authentication
- Print
- DarkLight
- PDF
Azure Automation is, in my opinion, a great way to automate your Azure environment management. You do that mainly through Runbooks. In the past years, I’ve created many of these runbooks to address requirements such as:
• Deleting expired resources based on a given tag
• Identifying service principals with credentials about to expire
• Periodically syncing a list of users based on updates to the Azure AD tenant
If you have used Azure Automation before, you probably didn’t like its authentication mechanism based on the RunAs account that much. I was waiting for when the Azure Automation service would support the use of Managed Identities. Well, that’s now possible, and you can use either a System-Assigned or User-Assigned Managed Identity! 😊
The problem with RunAs accounts
The main thing I didn’t like about RunAs accounts is the necessity to renew their certificates every once in a while. If you weren’t that rigorous, you would end up with expired certificates and runbooks that do not execute anymore. With Managed Identities, Azure takes care of that for you.
Using Managed Identities with newly created Automation Accounts
When you create a new Automation Account instance, no RunAs account is created. Still, there already is a System-Assigned Managed Identity that is created (you can check that by going to “Identity” under “Account Settings”). You can assign the required role to that Managed Identity for your runbooks to have the appropriate permissions.
You’ll need to add the following code into your runbooks so that they authenticate using the Managed Identity you’ve set up (this code is in PowerShell because that’s the scripting language I use when authoring my runbooks):
#Connect to Azure with your managed identity
$AzureContext = (Connect-AzAccount -Identity).context
#Set the Azure context to be used
$AzureContext = Set-AzContext -SubscriptionName $AzureContext.Subscription -DefaultProfile $AzureContext
Using Managed Identities with existing Automation Accounts
You can follow the same procedure for newly created Automation Accounts to use Managed Identities with existing Automation Accounts.
However, you’ll need one more step, which is deleting the RunAs Accounts (we don’t want to leave existing accounts with permissions unused in our tenant, do we? 😉):
In your Automation Account instance, go to “Run as accounts” (under “Account Settings”):
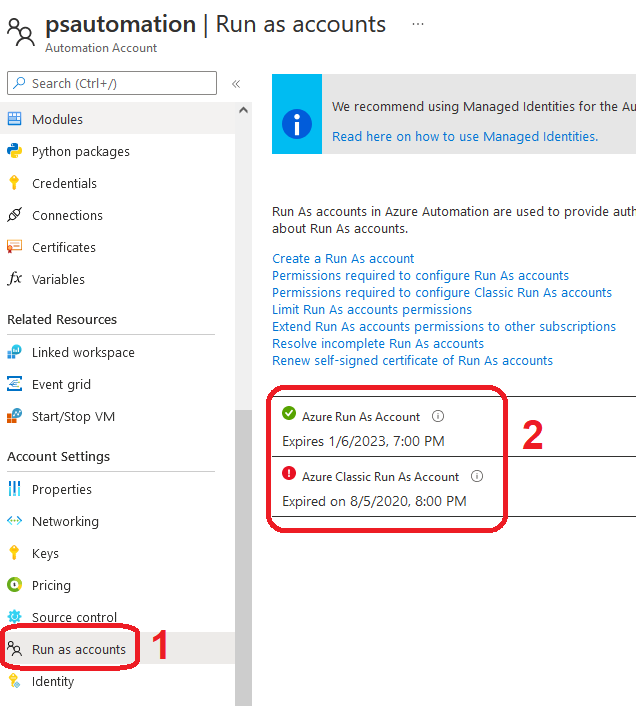
Then, select each configured RunAs account and delete it using the appropriate button:
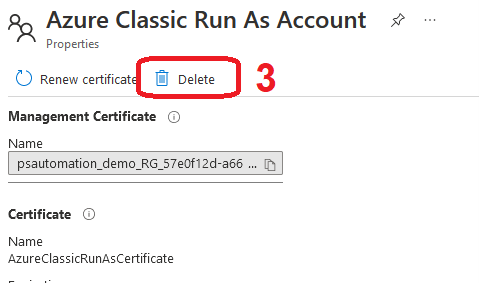
And, voilà!

